Last Updated on March 22, 2025
Need stronger security for your files?
In this guide, let’s talk about the critical features of SharePoint Online data protection.
Let’s get started.
Table of Contents:
Current Trends and Challenges in Data Security
As you know, new threats and technologies shape how organizations protect their data and information.
There are new key trends today in data security, such as the ones listed below that help combat emerging threats:
- Zero trust security model
- AI-powered threat detection
- Stronger data encryption
- Privacy regulations compliance
- Cloud security enhancements
Increasing cyber threats are still the worst challenges as attackers constantly develop more advanced and predictable methods.
Some examples include:
- Ransomware attacks
- Phishing scams
- Supply chain attacks
- Zero-day vulnerabilities
Unfortunately, even the best security tools struggle to keep up with evolving threats.
Organizations must stay proactive using AI-driven security, strict access controls, and continuous monitoring to reduce risks.
The truth is that cybercriminals only need one weak spot to break in, which makes cyber threats the most dangerous challenge.
Of course, we can still account for human error and insider risks here as employees can unintentionally expose data.
Sign up for exclusive updates, tips, and strategies
Critical Features for SPO Data Protection
Let’s start with this one:
1. Data Encryption
This is a security method that converts readable data into an unreadable format so only authorized users can access it.
Encryption in SharePoint Online is built-in and works automatically, and it provides:
- Encryption at rest
- Encryption in transit
- Customer key option
- Office 365 message encryption (OME)
Encryption helps in data protection as it prevents unauthorized access to the data, even if it’s intercepted or stolen.
That’s because, without the right decryption key, encrypted files remain unreadable.
This protects sensitive business information from cyber threats, insider risks, and accidental data leaks.
2. Access Controls and Permissions
If you have used SharePoint before, then you know that you can determine who can view, edit, or share data.
That’s part of access controls and permissions, and it can help prevent unauthorized use of sensitive information.
In SharePoint, this translates to:
- Role-based access control
- Permission levels
- Sharing restrictions
- Conditional access policies
- Audit logs and reports
For example, you can easily set up custom permission levels to prevent users from accessing sensitive files they don’t need.
This can be done in the advanced permissions settings of a site:
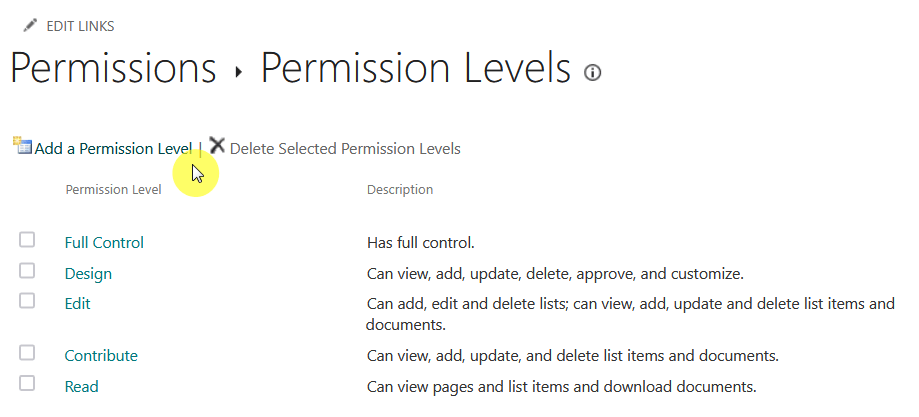
In effect, this will reduce accidental deletions, unauthorized edits, and data leaks.
3. Multi-Factor Authentication (MFA)
You’re probably already familiar with this security feature as it’s commonly used by many apps and websites today.
MFA practically requires users to verify their identity using multiple authentication methods before they can access SharePoint.
You can set MFA in Microsoft Entra ID (formerly Azure AD):
This provides:
- Two-step verification
- Authentication app support
- Biometric authentication
- Conditional access integration
The bright side here is that Microsoft implements security defaults in Microsoft Entra ID to enhance security across organizations.
When enabled, it will require all users to register for and use MFA, specifically through the Microsoft Authenticator app.
There’s also the new mandatory MFA for all user accounts accessing the Microsoft 365 admin center (started on February 3, 2025).
With MFA in place, it will prevent unauthorized access to SharePoint even if a hacker has a user’s password and details.
4. Data Loss Prevention (DLP) Policies
Basically, with DLP, you can create rules to help prevent sensitive information from being shared, leaked, or lost.
For this, you need to go to the Microsoft Purview Compliance Center and find the dedicated data loss prevention section.
You will then find an option to create a DLP policy from there:
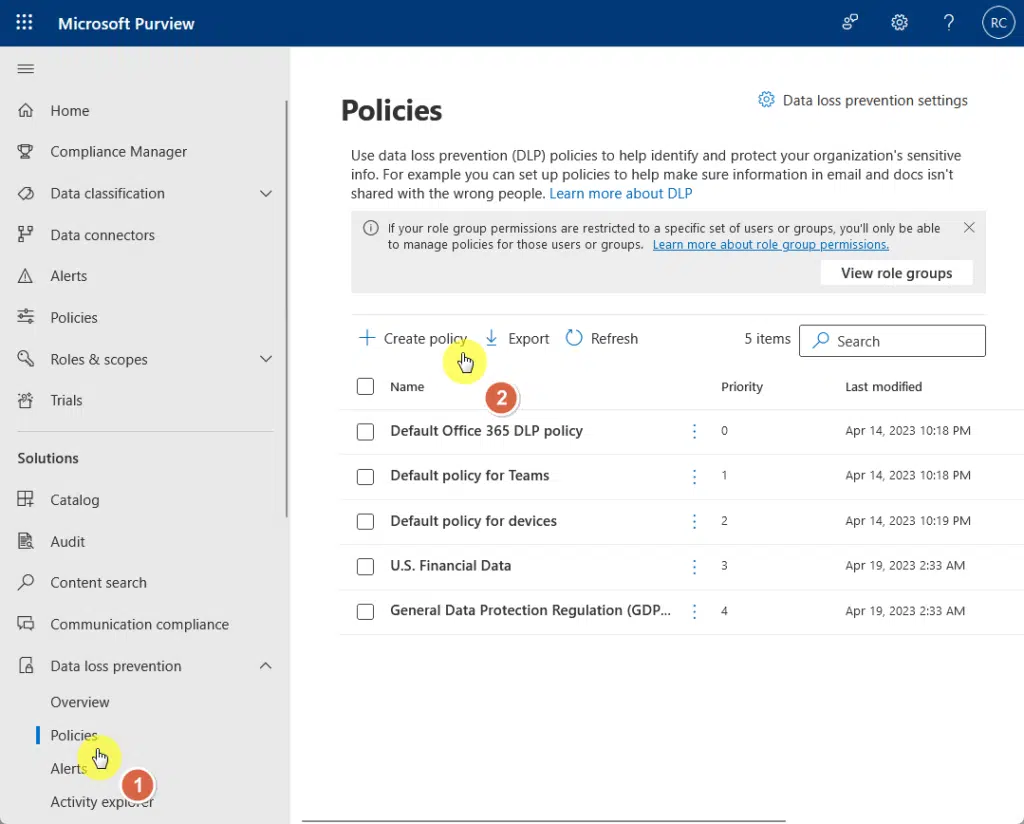
The DLP feature in Microsoft 365 will allow administrators to:
- Identify sensitive information
- Apply automated rules
- Send policy alerts
- Protect shared files
- Monitor data activities
What’s also nice is that SPO provides a default DLP policy that automatically identifies and manages sensitive information.
This includes credit card numbers or content that match specific regulatory templates like U.S. HIPAA.
Note that this default policy is active even before you create any custom DLP policies and is fully customizable to your needs.
SharePoint Online also has a Sensitive by Default feature.
Basically, it prevents external access to newly uploaded files until they’re scanned for sensitive content by DLP policies.
Unfortunately, there’s no UI for it if you want to manage it as the only way for now is to use SPO Management Shell.
5. Information Rights Management (IRM)
IRM protects documents and files by restricting how they can be accessed, edited, and shared even after a file is downloaded.
It kind of works like a policy that applies security controls to files and documents and extends even when they’re downloaded.
You will need to activate the Rights Management Service first in the Microsoft 365 admin center, then enable IRM in SharePoint.
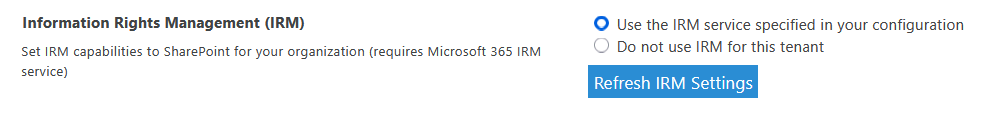
After that, you will be able to apply IRM to a specific document library or list. 🙂
In the context of SharePoint Online, IRM will provide:
- Restriction on copying and printing
- Blocking forwarding and sharing
- Setting expiration dates
- Applying persistent encryption
- Watermarking documents
IRM should prevent unauthorized distribution and misuse of sensitive data.
Unlike standard permissions, which apply only while a file is in SharePoint, IRM will remain even after a file is downloaded.
If you have intellectual property, financial records, and business-sensitive information in SPO, this is a critical feature to have.
Advanced Security Measures and Best Practices
I also want to share a few advanced measures and policies that go beyond the basic features like policies and controls.
Starting with this:
Zero Trust Security Model
I mentioned this earlier as one of the current trends we have today.
This assumes no user, device, or application is trusted by default, even if they’re inside the corporate network.
Unfortunately, SPO doesn’t have a built-in, one-click feature for this, instead, you need to combine multiple tools.
We’re talking here about:
- Microsoft Entra ID
- Microsoft Intune
- Microsoft Purview Information Protection
- Microsoft Defender for Cloud Apps
For example, you can create session policies in Defender for Cloud Apps as well as implement anomaly detection policies.
You need to watch this out closely though since zero trust principles can be a hassle for users with the need for constant authentications.
Imagine having to verify your identity multiple times a day, getting logged out often, and not having immediate access to files.
The key is to balance it with usability by implementing smart policies like adaptive authentication and seamless single sign-on.
Conditional Access Policies (CAPs)
These policies are security rules in Microsoft Entra ID that control how and when users can access apps like SharePoint Online.
The way they work is that they dynamically enforce security measures based on factors like user location, device compliance, etc.
You can set this up in Microsoft Entra ID:
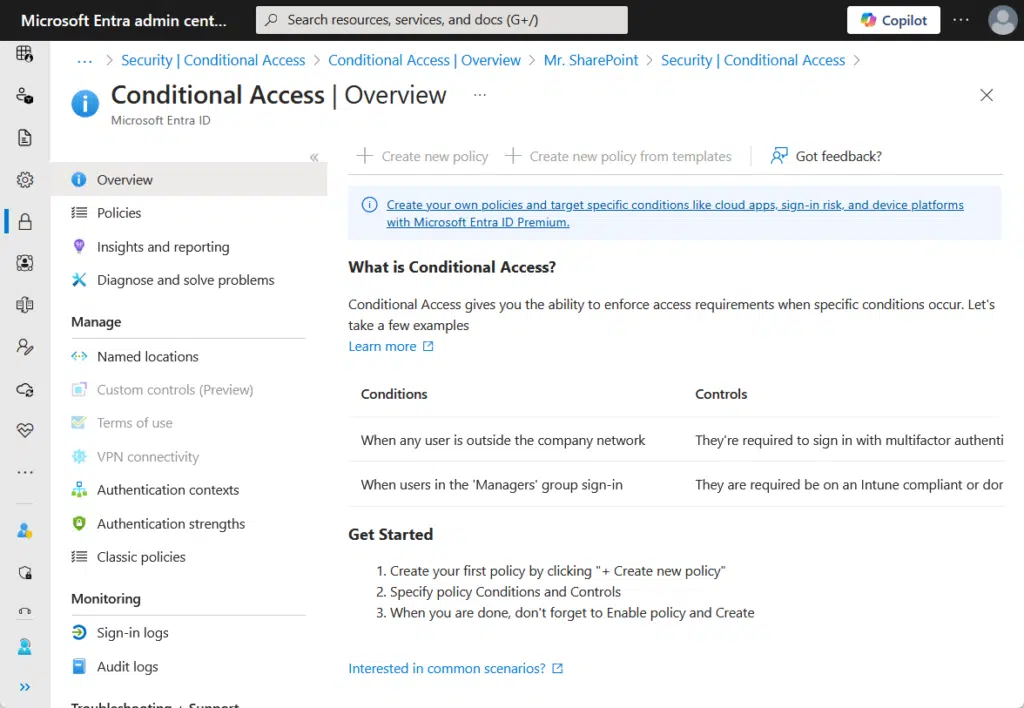
Conditional access policies can help:
- Block or restrict risky logins (like from unknown locations or devices)
- Enforce MFA based on risk levels
- Require compliant devices (only allow managed/encrypted devices)
- Prevent access from outdated or insecure applications
For example, you might be in a company that wants to protect SPO but doesn’t want to annoy office-based employees.
You can then set a policy requiring MFA only for remote or unknown devices to allow easy access while securing remote logins.
This is a good practice because organizations continuously adjust and refine policies based on new threats and needs.
Integration with Third-Party Security Tools
SPO, and Microsoft in general, have great built-in protections in place, unfortunately, you might want more than what they offer.
For example, third-party tools can help by:
- Adding AI-drive anomaly detection beyond Microsoft’s default settings
- Providing extended and more granular DLP policies
- Automating threat responses with customized security workflows
- Getting deeper logging for industry regulations
Some examples of what you can use include Microsoft Defender for Cloud Apps, Splunk, Symantec DLP, and CrowdStrike Falcon.
For example, you can use Microsoft Defender for Cloud Apps to provide real-time monitoring and threat detection for SPO.
It’s useful in identifying unusual activities like mass file downloads, unauthorized sharing, or access from risky locations.
Another example is Splunk, which can help centralize and analyze security logs from SPO and other Microsoft 365 services.
It can detect hidden threats, insider attacks, and compliance violations by linking security events, enabling faster response.
The point here is that integrating third-party tools adds layers of protection to SharePoint, though it also requires expert configuration.
Regular Auditing and Monitoring
I consider this advanced because it requires continuous oversight, proactive threat detection, and automated alerting.
The good news is that SharePoint Online has built-in auditing and monitoring tools, the downside is that they have limitations.
With SharePoint Online’s features alone, you can have:
- Unified audit log
- Alert policies
- Microsoft Defender for Microsoft 365
- Access reports
For example, you can enable the audit log tracking feature in Microsoft Purview:
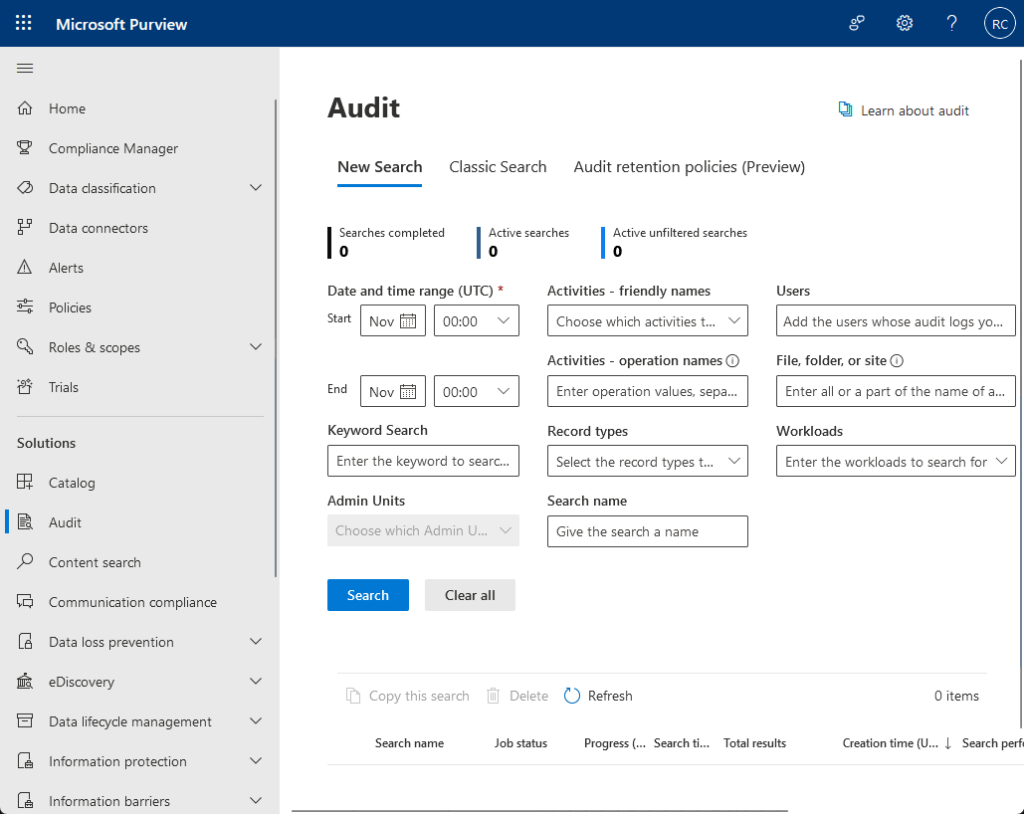
Unfortunately, SharePoint-only monitoring has shorter log retention, no advanced threat detection, and limited automation.
There are a lot of third-party tools though that you can use if you want deeper log analysis and long-term data retention.
For example, there’s SolarWinds Server & Application Monitor (SAM) that’s considered one of the best out there.
It has:
- Comprehensive app monitoring
- Customizable alerts and reports
- Performance metrics
- Environment mapping
- Integration capabilities
Other examples of third-party tools you can use are ManageEngine SharePoint Manager Plus and Paessler PRTG Network Monitor.
Educating Users on Security Best Practices
Personally, this is the best security investment you can make.
Even with advanced security measures in place, human error remains a major risk to the organization’s data.
I recommend implementing regular training programs to teach employees about:
- Phishing threats
- Secure file sharing
- Proper use of permissions
In your training, encourage using MFA, recognizing suspicious activities, and reporting security incidents.
You can create a culture of proactive data protection by making security awareness a part of daily operations in your organization.
Do you have any questions about data protection features in SharePoint Online? Let me know below.
For any business-related queries or concerns, contact me through the contact form. I always reply. 🙂

