Last Updated on February 17, 2024
Recently saw advanced management in your SharePoint admin center?
In this article, you will learn the basics of advanced management, its features, and how those features can help.
Let’s get started.
Table of Contents:
- Introduction to Advanced Management
- Advanced Access Policies
- Advanced Sites Content Lifecycle Management
Introduction to Advanced Management
Basically, this add-on will enhance your control and oversight of SharePoint and OneDrive environments.
There are three basic benefits that advanced management brings:
- Enhance security measures
- Improved data governance
- Streamlined document management
At the core of advanced management is an emphasis on tightening security across your sites and OneDrive.
As for the feature itself, it’s been available for a while now — however, you may have seen it recently in the admin center:
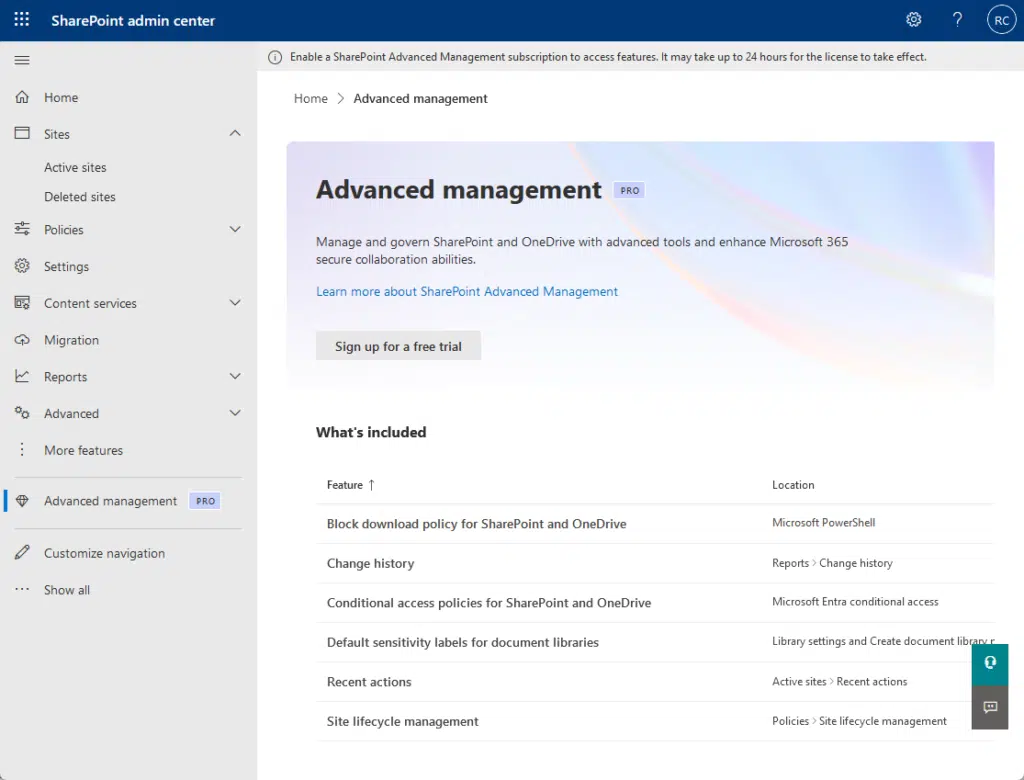
It’s more than just a set of tools though, it would help you manage your SharePoint environment proactively.
SharePoint advanced management (SAM) isn’t free — but it’s generally available as a per-user license.
You can purchase the add-on from the Microsoft 365 admin center (though each user must also have a SharePoint K, P1, or P2 license.
You can find more information on the announcement of advanced management on Tech Community.
Note: Since I didn’t get this license for my test environment yet, the screenshots I have also came from the same source.
Sign up for exclusive updates, tips, and strategies
Advanced Access Policies
Advanced access policies offer a suite of customizable security measures.
These measures are designed to enhance the control administrators have over:
- Who can access specific content
- how those content are accessed
All the policies here are tailored to secure sensitive information from unauthorized access or leakage.
Data access governance (DAG) insights is a comprehensive solution for overseeing data access and security.
It’s specifically designed to help against the challenge of data sprawl and the potential oversharing of sensitive data.
Data access governance reports address these concerns with insights that help you in governing SharePoint data access.
Using these reports, you can:
- Identify sites containing overshared or sensitive content
- Assess and implement necessary security and compliance policies
Key Features and Requirements
Before you can dive into the insights, you have to comply with the requirements:
- Your organization must have a Microsoft 365 E5 or Microsoft Syntex-SharePoint Advanced Management subscription.
- Only admins with Microsoft 365 E5 licensing can access the data access governance reporting.
There’s a catch though — those admins won’t have access to other SharePoint advanced management features.
Here are the insights offered by the reports:
- Sharing link reports: Help pinpoint potential oversharing issues by showing sites where users have created numerous sharing links
- Sensitivity labels for file reports: Identify sites storing Office files with applies sensitivity labels for appropriate policies
The sharing link reports include the “anyone” links, “people in the organization” links, and “specific people” links.
For operational guidance:
- You can run all reports simultaneously or select individual reports only
- You can view reports directly or download them as a .csv file for up to 10,000 sites
Generating reports can take a few hours, and each report can only be run once every 24 hours.
Limitations and Considerations
Take note of DAG insights limitations and considerations:
- Reports are only effective if non-pseudonymized report data is enabled for your organization.
- Data might be delayed by up to 48 hours, and in new tenants, it may take several days for data to become available.
You can adjust or enable non-pseudonymized report data, though it will require global administrator access.
RAC policy enables you to restrict access to SharePoint sites and content exclusively to users within specific groups.

Simply speaking:
If a user isn’t part of the designated group, they won’t be able to access the site or its content, even with prior permissions or shared links.
This applies to both group-connected (e.g., Microsoft 365 Groups and Teams) and non-group-connected sites.
Important Notes and Considerations
- Implementing a RAC policy might take up to an hour to take effect, especially for Microsoft 365 multi-geo users
- Adding users to security groups doesn’t grant them access to Teams channels automatically
- Shared and private channels sites require individual site access restriction configurations (not affected by team-wide policies)
- You can monitor site access restriction activities through audit events in the Purview compliance portal
With RAC policies, your sites and their content are only accessed by the intended audience.
Restricted Access Control (RAC) Policy (OneDrive)
Similar to sites, OneDrive accounts also get overshared, a lot.
This policy will enable you to fine-tune access and sharing permissions for OneDrive content in your organization.
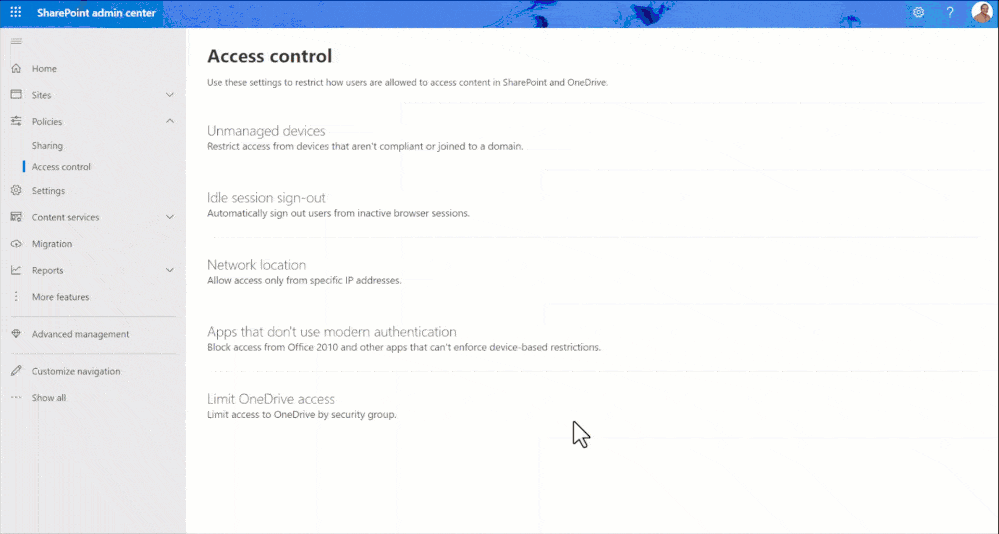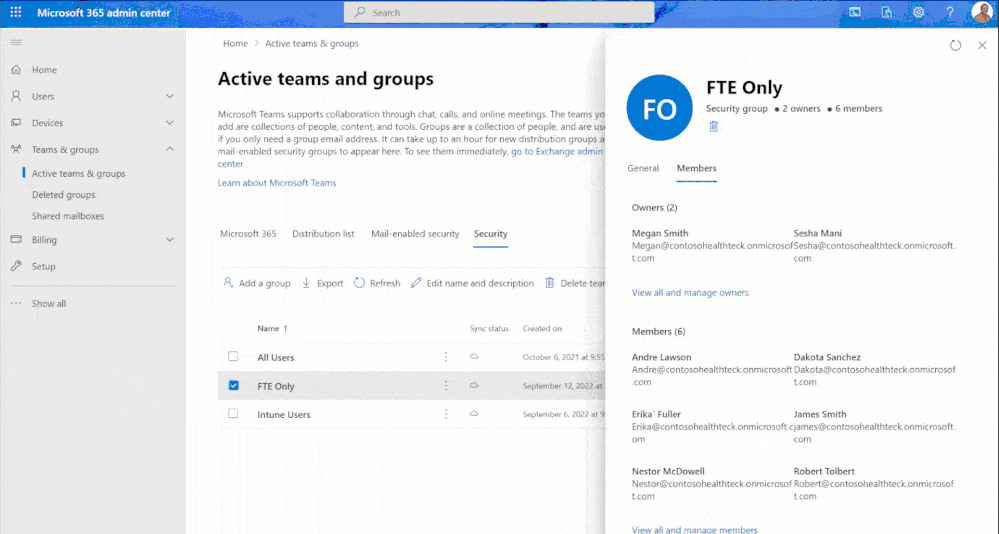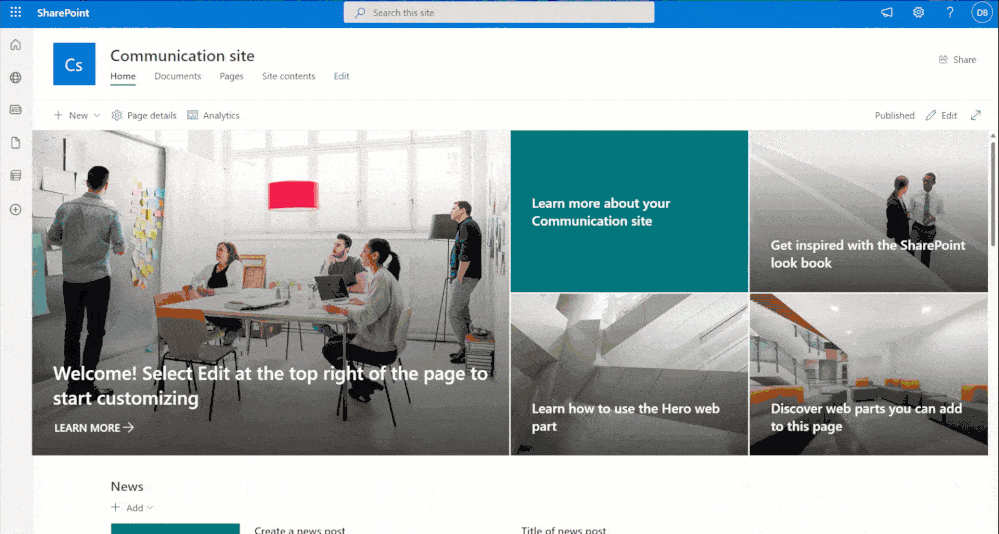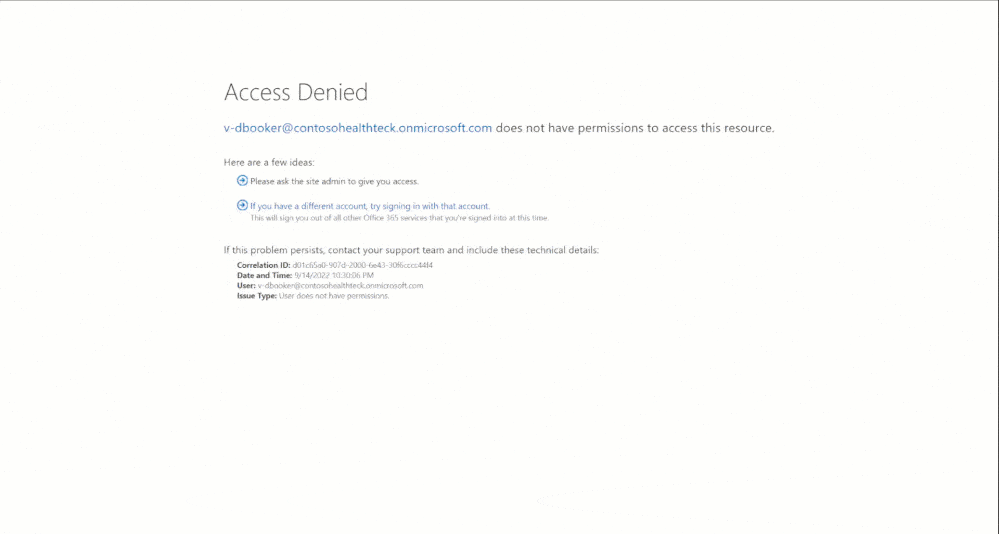
In a nutshell, the RAC policy for OneDrive allows you to:
- Restrict access and sharing of OneDrive content exclusively to users within specified Microsoft Entra ID security groups
- Ensure that users outside these security groups, even if they are licensed for OneDrive, cannot access their own OneDrive or any shared OneDrive content under this policy
Key Requirements and Considerations
Before you can implement this policy, your organization has to subscribe to one of the following:
- Microsoft Syntex – SharePoint Advanced Management
- Office 365 E5/A5
- Microsoft 365 E5/A5
You also need to take note of the following:
- Users not in the specified security groups will lose access to their OneDrive and any content shared with them
- Sharing will be permitted only within the specified security groups
Monitoring and Auditing
To help you oversee the enforcement of the RAC Policy, audit events are available in the Microsoft Purview compliance portal.
These events include:
- Enabling restricted OneDrive access and sharing
- Disabling restricted OneDrive access and sharing
This feature allows for a comprehensive overview of how the restricted access policy is being applied.
With the RAC policy for OneDrive, you can rest easy that your team’s collaboration is both productive and secure.
Conditional Access Policy (Sites and OneDrive)
Still has a similar effect with the previous policies, this one leverages Microsoft Entra authentication contexts.
The policy then enforces stringent access conditions so only authorized users can access sensitive information.
Requirements for Setting Up Conditional Access
Before diving into the setup, your organization must hold one of the following licenses:
- Microsoft Syntex – SharePoint Advanced Management
- Microsoft 365 E5/A5/G5
- Microsoft 365 E5/A5 Compliance
- Microsoft 365 E5 Information Protection and Governance
- Office 365 E5/A5/G5
Policies and Limitations
Conditional access policies allow you to:
- Apply policies directly to SharePoint sites
- Apply them through a sensitivity label
Take note that these policies cannot be applied to the root site in SharePoint.
For the limitations:
- Some apps, including older versions of Office, do not support authentication contexts
- Apps like Viva Engage, Teams web app, and the OneNote app, along with certain Teams functionalities, face limitations when an authentication context is applied.
- The OneDrive sync app won’t sync sites with an authentication context.
Using such policies can significantly enhance the security and compliance posture of your environment.
These measures ensure that access is meticulously controlled, aligning with your organization’s data protection strategies.
With this new feature, it’s now possible to apply more specific and granular security controls on a document library.
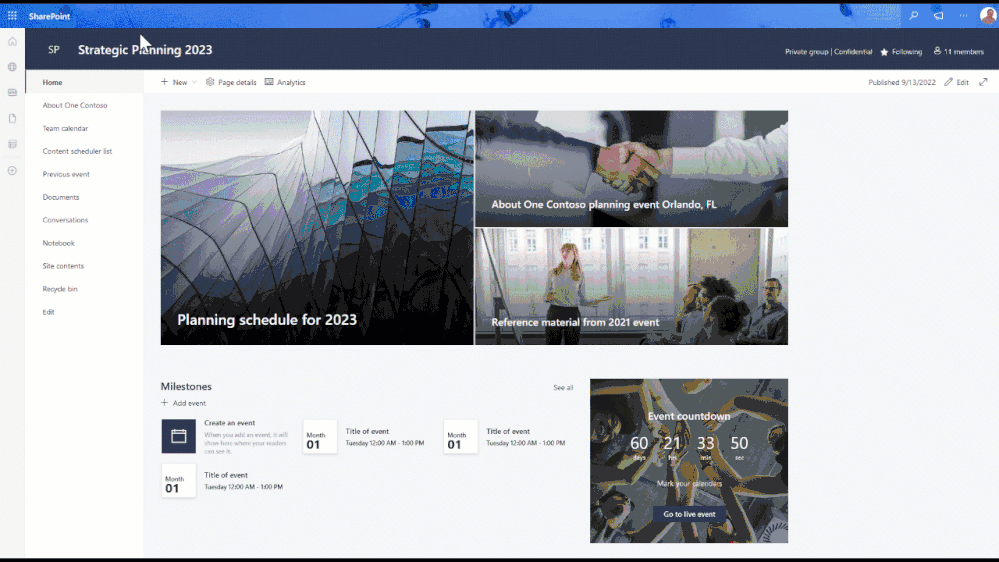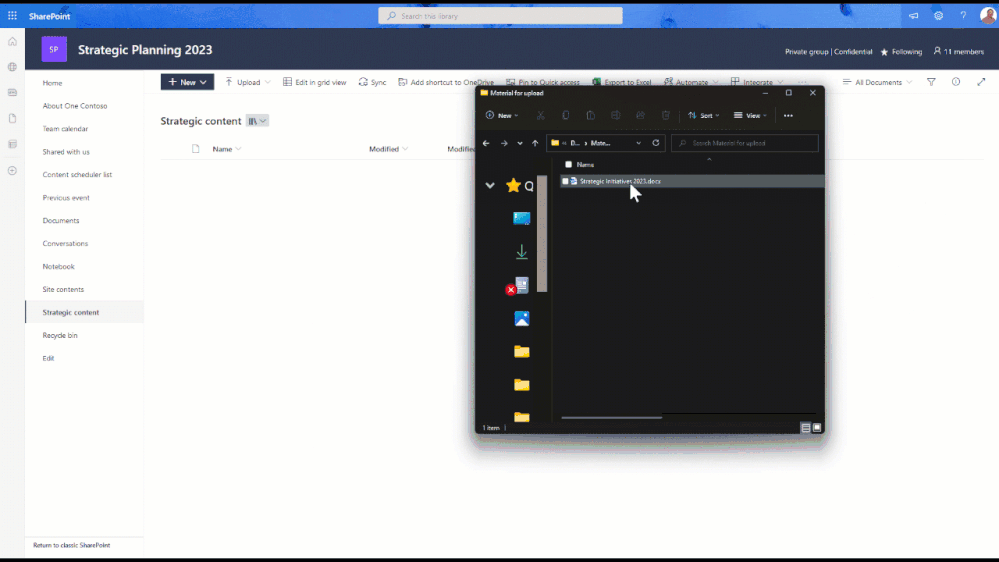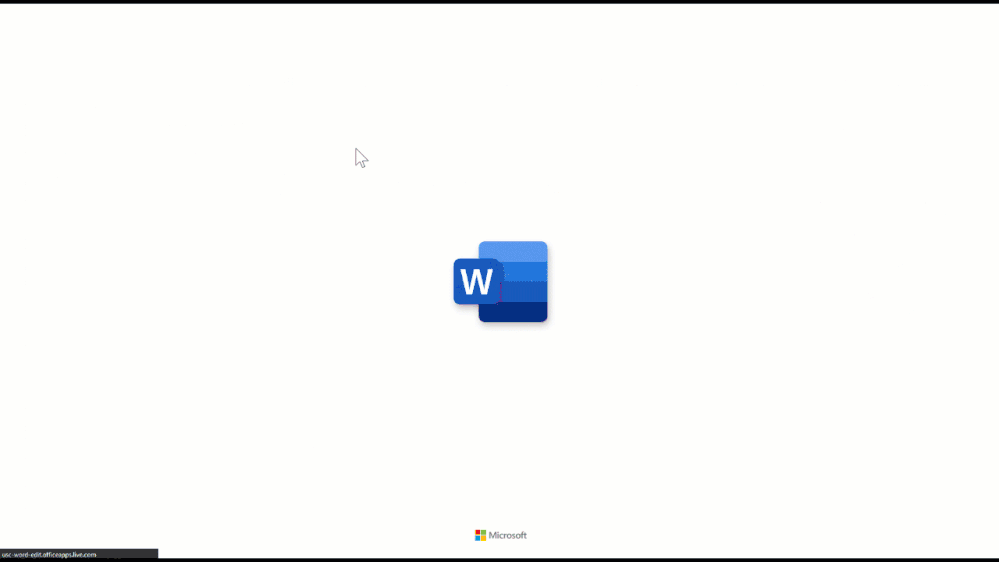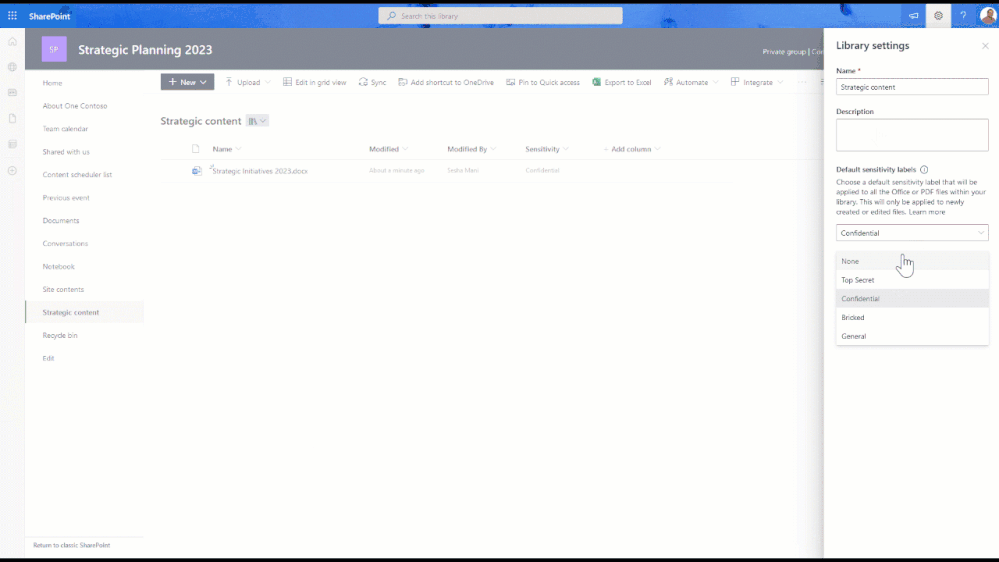
You can now do the following:
- Automatic labeling of documents with the default label (even if a document has a lower priority label)
- Offer a basic level of protection without the need for content inspection.
Let’s say a “confidential” label is set as the default for a certain document library.
If a user uploads a new file with a “general” label, the library will upgrade the label to “confidential”.
Requirements and Auditing
Well, as usual, you need certain licenses such as Microsoft 365 E5, Office 365 E5, or Microsoft Syntex – SharePoint Advanced Management.
Other than that, you need to make sure that:
- Sensitivity labels are created, and published, and include the label scope of items and files.
- Sensitivity labels for Office files in SharePoint and OneDrive are enabled.
- SharePoint Information Rights Management (IRM) is not enabled for the library (it’s incompatible with default sensitivity labels).
For monitoring and auditing, you can check the sensitivity labels applied to files (they will indicate automatic labeling).
You can use the compliance portal to audit label application events — look for the applied sensitive label file.
Considerations
I also want to stress out a few things (reminders actually) connected to default labels:
- The default label doesn’t affect files already saved in SharePoint unless edited.
- There might be a delay in applying the default label using the “save as” function unless co-authoring for encrypted files is enabled.
- Some configurations, like user-defined permissions or user access expiration, are unsuitable for SharePoint and therefore don’t support default labeling.
If necessary, you can also disable this feature for your tenant using the Set-SPOTenant cmdlet.
This will remove the option to configure default sensitivity labels for document libraries, but previously applied labels will remain unaffected.
Advanced Sites Content Lifecycle Management
This one focuses on the comprehensive management of SharePoint sites throughout their lifecycle.
Let’s look at the specific features one by one:
Inactive Sites Lifecycle Management Policy
If you need to find inactive sites before, you need to check out individual sites and message their owners.
But with this feature, you will be able to create a site policy that targets specific inactive SharePoint sites and trigger alerts.
Like any policy, there are two phases involved:
- Automated discovery
- Tailored policy application
The policy enables the automated identification of sites that have transitioned to an inactive state over time.
Admins can create policies for these sites to facilitate a more organized and secure SharePoint environment.
Key Features
Here are the key features:
- Alerts to site owners: Once a site is deemed inactive, the policy triggers alerts to site owners, empowering them to decide whether to keep, delete, or undertake other actions on these sites.
- RAC application: To further secure content and eliminate unauthorized access, you can apply RAC policies on these inactive sites.
- Teams and SharePoint integration: For sites connected to Teams, inactivity is assessed by evaluating user actions across both platforms, ensuring comprehensive coverage.
When a site is deemed inactive, the policy alerts site owners (and lets them decide the action).
You can apply RAC policies on these inactive sites to further secure and eliminate unauthorized access.
What’s even cooler is that this policy evaluates user actions on the SharePoint site and even on Teams.
It’s important to keep track of changes and actions — including admin actions.
Fortunately, this new feature allows admins to review their most recent actions to Sharepoint site properties.
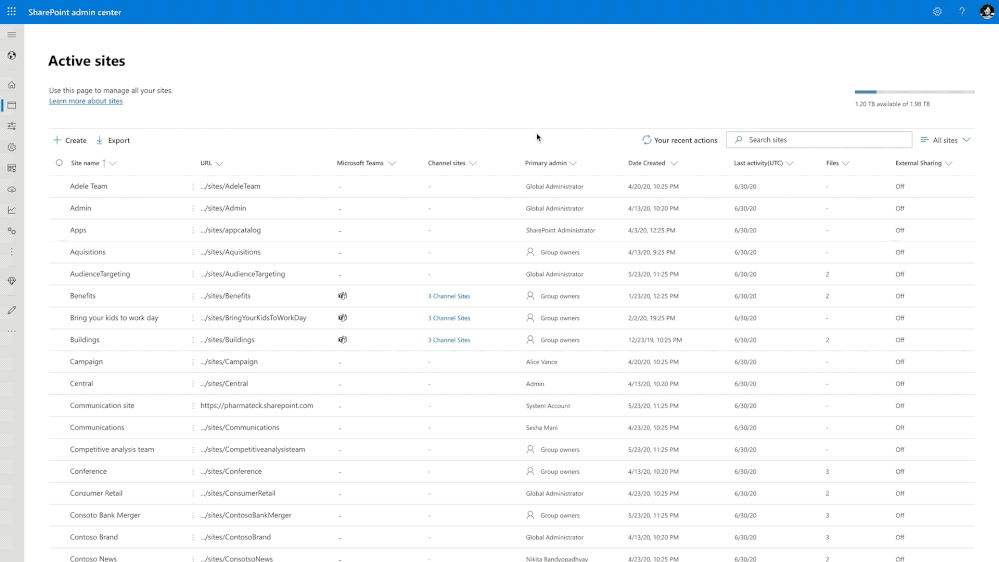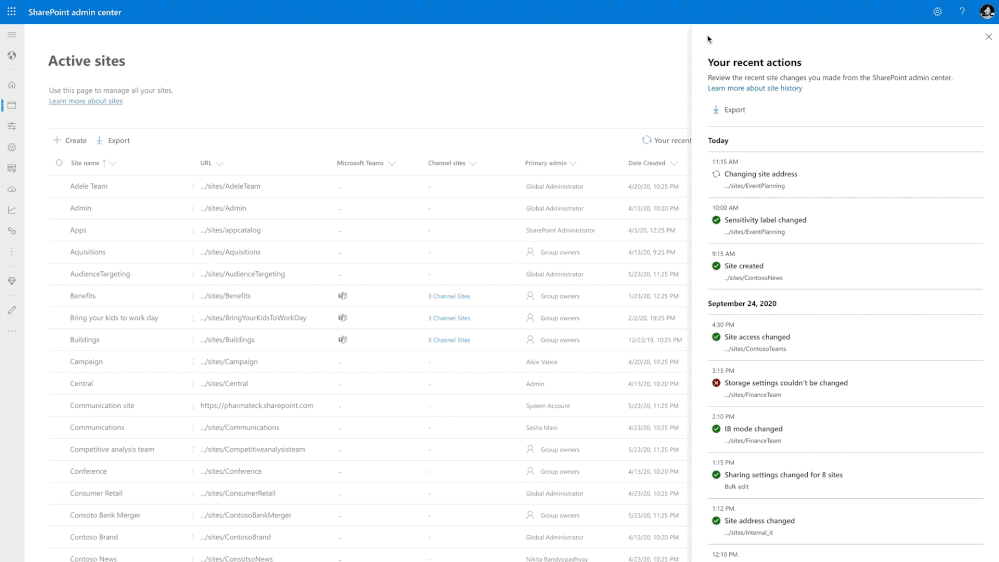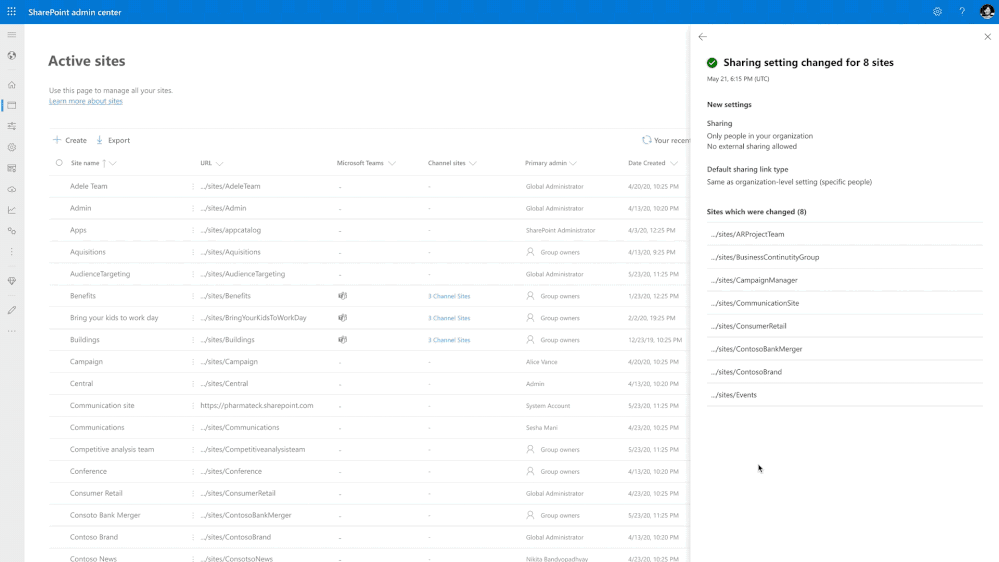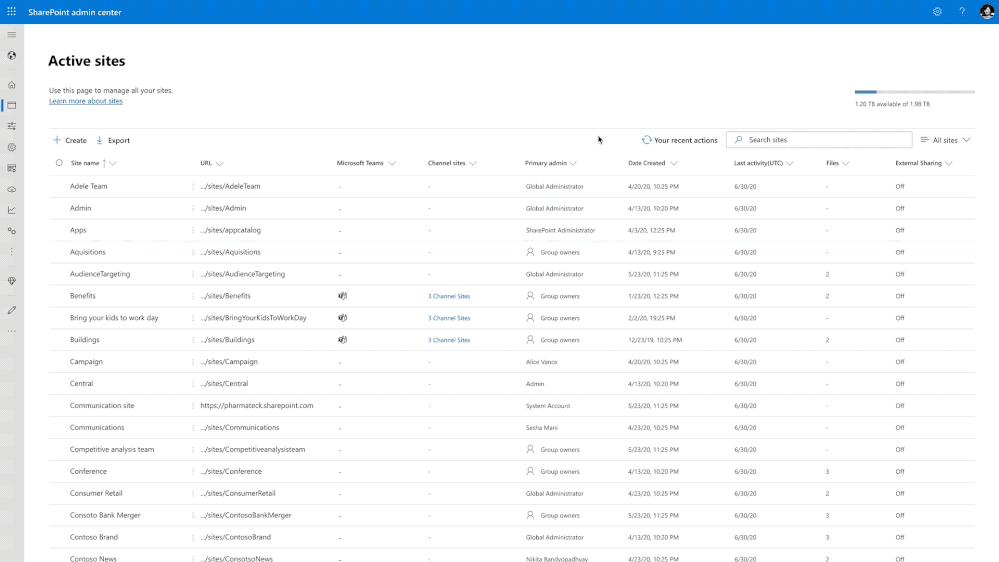
There are two key features here:
- Easily view changes made to site properties like site name, deletion, and storage quota adjustments
- No clutter from organization-level or other admin actions since you can only see changes you have made
Requirements and Access
To use this feature, your organization must have Microsoft Syntex – SharePoint Advanced Management.
It’s also important to note that:
- The recent actions panel is exclusive to actions you perform, enhancing personal accountability and tracking.
- Global Reader and GDAP administrators are restricted from viewing detailed action histories, such as previous and current values of administrator actions.
Limitations
There are two important limitations here:
- Actions are session-specific
- Actions not completed before browser closure aren’t recorded
In short, once you close the browser or sign out, the history clears — export records for long-term tracking.
While failed actions appear in the panel, they’re removed upon session end and are not included in the exported .csv file.
Sites History
This one is pretty simple:
You can know the full history of activities made by its site owners and make troubleshooting easier.
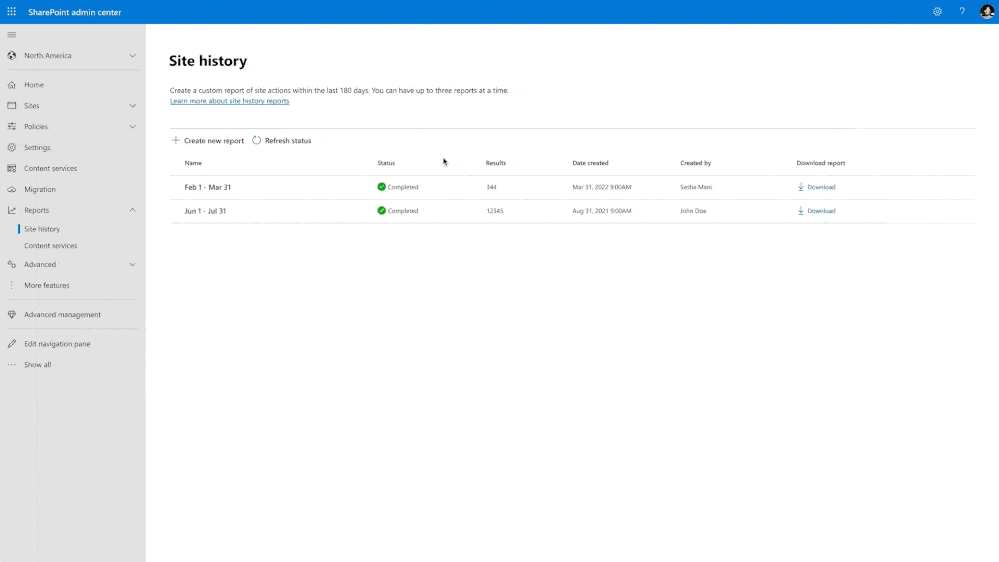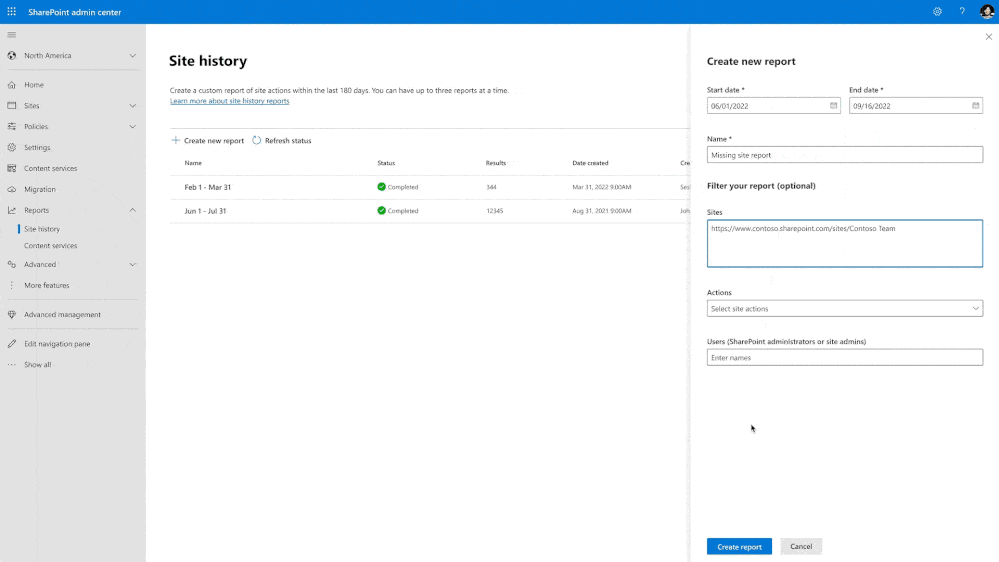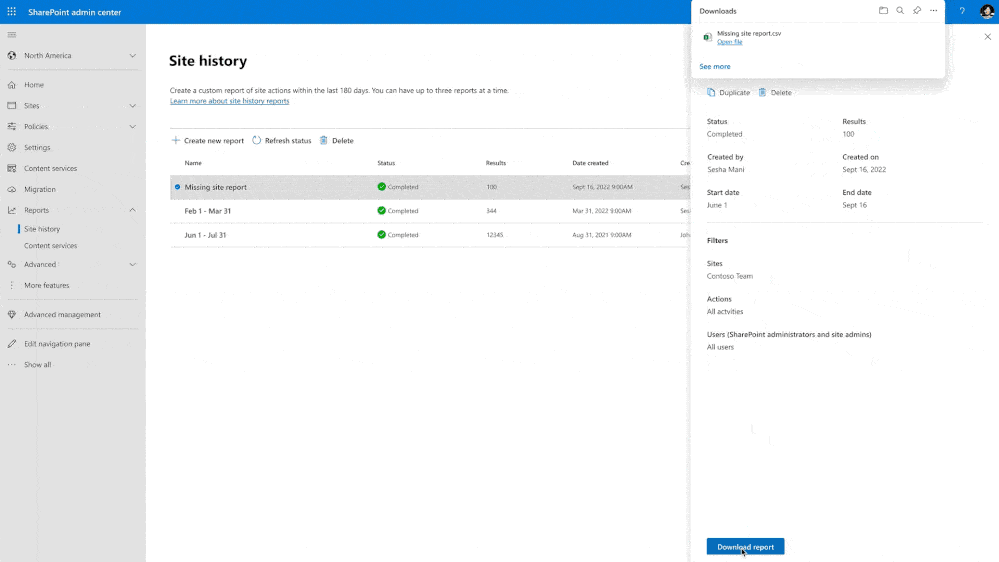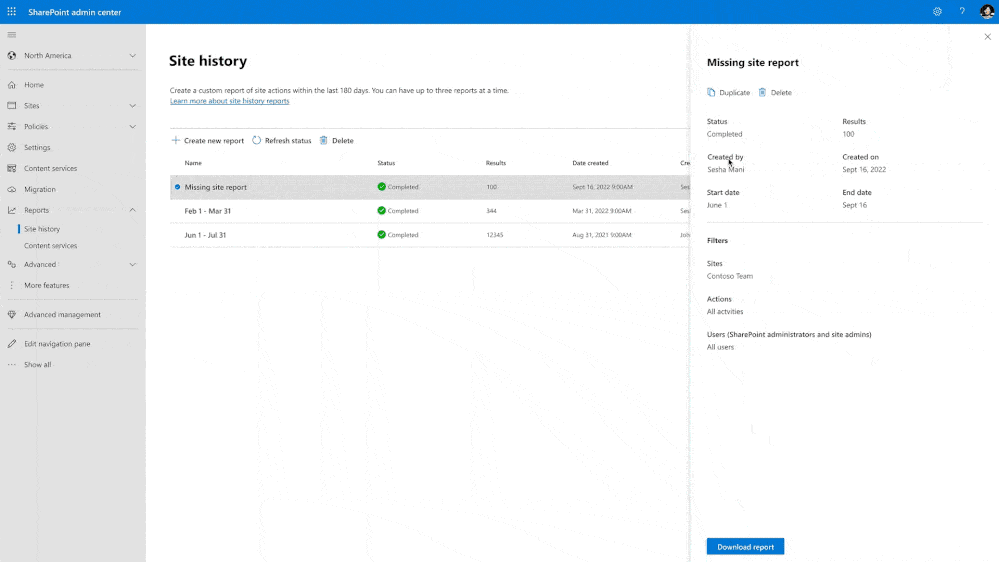
The site history feature is designed to:
- Record each modification made to site properties by site owners and admins
- Allow you to investigate and resolve issues much faster than before
Once you get a SAM license, this feature will automatically be added to your tenant.
Block Download Policy (Sites and OneDrive)
From the name itself, this feature would prevent unauthorized download and sharing of files.
There are four key features here:
- Restrict the ability to download, print, or sync files from SharePoint sites or OneDrive
- Users can view files through their browser but cannot take actions that would move data out of SharePoint or OneDrive
- Restricts content access through apps, including Office desktop applications.
- When web access is restricted, users receive a notification about the download, print, and sync restrictions, guiding them to contact IT for assistance.
This policy helps mitigate the risk of data leakage by ensuring that sensitive information is not downloaded or shared inappropriately.
If you have more questions about SharePoint Advanced Management, feel free to leave a comment.
For business inquiries or any business concerns, please use the site’s contact form. I’ll reply promptly.

