Last Updated on January 15, 2025
Need to implement DLP in SharePoint?
In this guide, you will learn about data loss prevention in SharePoint Online, the core principles, how to implement it, and more.
Let’s get started.
Table of Contents:
As you may know, data loss in a SharePoint environment can be a critical concern for any organization.
It doesn’t only bring inconvenience — it can pose significant risks to business operations and data security.
On the bright side, understanding the root causes is the first step toward effective prevention.
Here are some common causes of data loss:
- User errors: Accidental deletion or mishandling of files due to user mistakes
- Security breaches: Vulnerability to cyber-attacks in the cloud, leading to unauthorized access and potential data loss
- Misconfigured workflows: Errors in automated processes, especially in complex SharePoint setups
- Corrupted files: Data loss due to file corruption caused by various factors
- Inadequate backups: Risk of data loss when regular backups are neglected
Learning these causes will enable you and your organization to reduce the risks of data loss proactively.
Sign up for exclusive updates, tips, and strategies
The short of it is that:
Data loss prevention (DLP) protects sensitive information from being lost, misused, or accessed by unauthorized users.
Here are the core principles of effective DLP strategies:
1. Identifying Sensitive Data
The foremost principle in DLP is to identify what constitutes sensitive data within your organization accurately.
This could include:
- Personally identifiable information
- Financial records
- Confidential business documents
It could also include any other data that, if exposed, could harm the organization or individuals.
👉 Related: How to Create Sensitivity Labels in Microsoft 365
2. Categorization and Contextual Awareness
Then, sensitive data should be categorized based on its level of sensitivity and the context in which it is used.
This includes:
- Classifying sensitive data with high-level security due to its critical nature.
- Differentiating between internal communications may require less stringent controls.
- Recognizing the varying sensitivity levels of data, such as public, internal, confidential, and strictly confidential.
For example:
Financial data might require stricter controls compared to general internal communications.
3. Least Privilege Access
Follow the principle of least privilege — where users have access only to the data necessary for their role.
Key practices involve:
- Conducting regular audits to ensure user access levels are appropriate and not overly permissive.
- Reviewing and adjusting permissions periodically to minimize the risk of unauthorized data exposure.
- Ensuring that any changes in roles or responsibilities are reflected promptly in access rights.
Regular audits of user access levels help prevent data exposure due to excessive permissions.
👉 Related: How to View SharePoint Online Audit Logs: Beginner’s Guide
4. Real-time Monitoring and Alerts
Implement real-time monitoring of data transactions within SharePoint Online.
Set up alerts for any unauthorized access attempts or policy violations.
Effective measures include:
- Setting up alerts for any signs of unauthorized access attempts or policy breaches.
- Monitoring data transactions continuously to detect and respond to potential threats promptly.
- Using advanced analytics to identify unusual patterns that might indicate a security issue.
Real-time monitoring helps in quickly identifying and mitigating potential data loss incidents.
👉 Related: How to Set Up Sharepoint Email Notification Alerts
5. Integration with Overall Security Posture
DLP should not be siloed but integrated with the organization’s overall cybersecurity strategy.
This integration ensures that DLP policies are aligned with other security measures, such as:
- Firewalls
- Intrusion detection systems
- Antivirus software
6. Continuous Review and Adaptation
Due to evolving digital landscapes and dynamic data, DLP strategies require continuous review and adaptation.
This requires:
- Regularly updating DLP policies to address new types of sensitive data.
- Adapting to changes in business processes that impact data handling and security.
- Staying abreast of technological advancements and evolving cybersecurity threats.
As new types of sensitive data emerge or as business processes evolve, DLP policies should be updated to remain effective.
Implementing data loss prevention involves a series of steps to protect sensitive data.
Here’s a structured approach to effectively implement DLP in your SharePoint environment:
Step 1: Assess your data
The first step in DLP is to understand and identify the types of data your organization stores in SharePoint Online.
This assessment should focus on:
- Identify sensitive data: Determine what data is considered sensitive in your organization.
- Data auditing: Conduct an audit of your SharePoint Online environment to locate where sensitive data is stored.
- Classification: Classify data based on sensitivity.
SharePoint Online offers data classification options that can be utilized to label data accordingly.
Step 2: Create DLP policies
Once you have a clear understanding of the sensitive data, the next step is to create DLP policies.
You need to go to Microsoft Purview, which you can access from Microsoft 365 admin center > compliance:
👉 Related: Microsoft Compliance Center: Microsoft Purview Basic Guide
From there, open the data loss prevention solution > go to policies where you can create a new one.
This is also where you can see all previously created DLP policies.
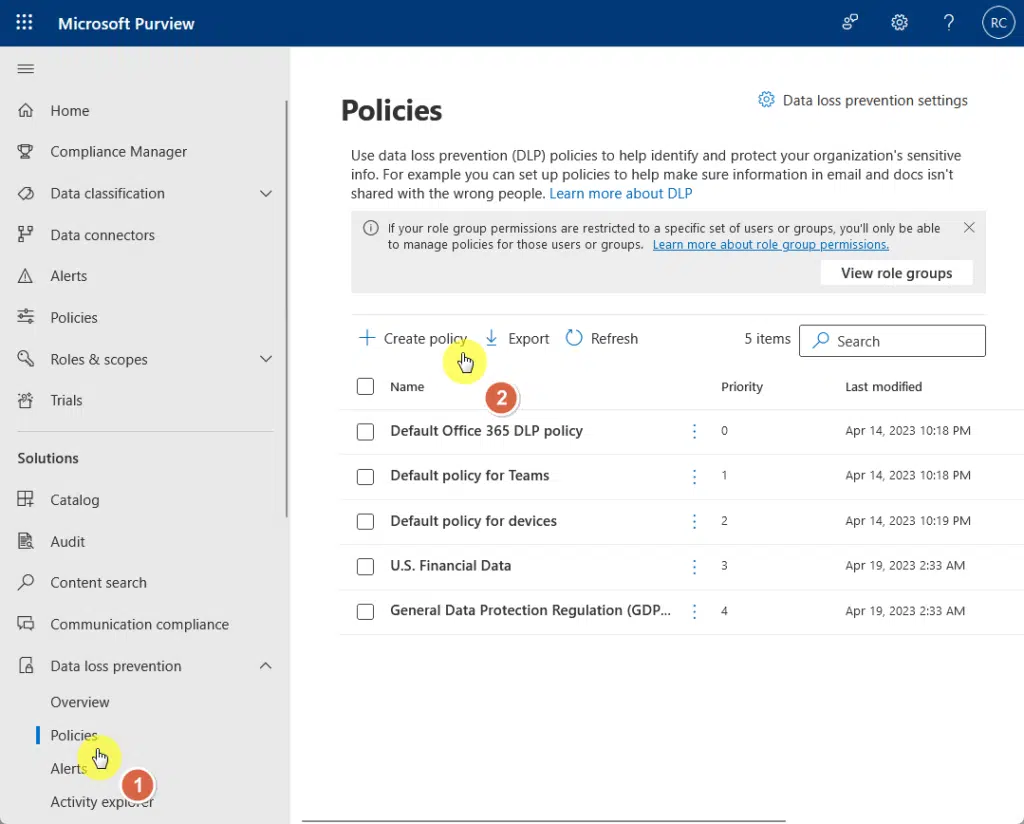
You can then start with a template (choose from the categories) or create a custom policy.
If the policy you want to create has a template, I suggest you do that to save time.
Otherwise, just select the custom option:
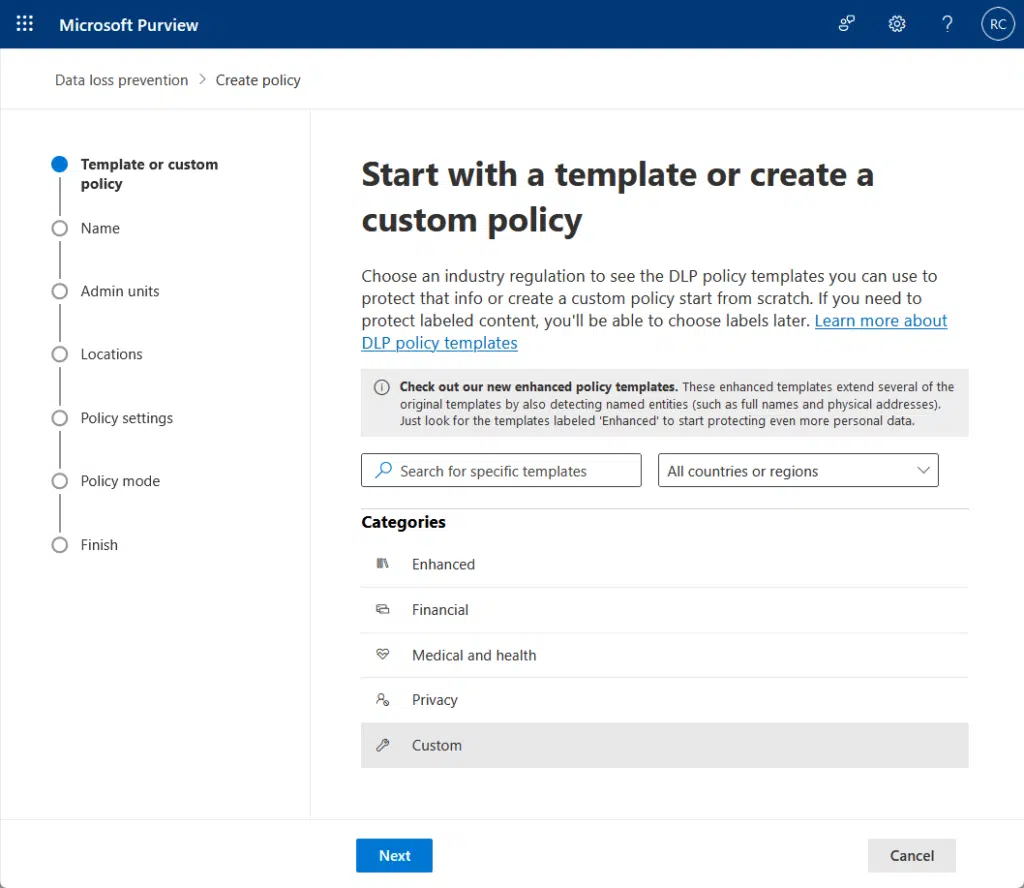
From there, just blitz through the applicable settings:
- Admin units
- Locations and repositories
You will get to the page where you will be able to add rules.
These rules will define the type of sensitive information that the policy will protect.
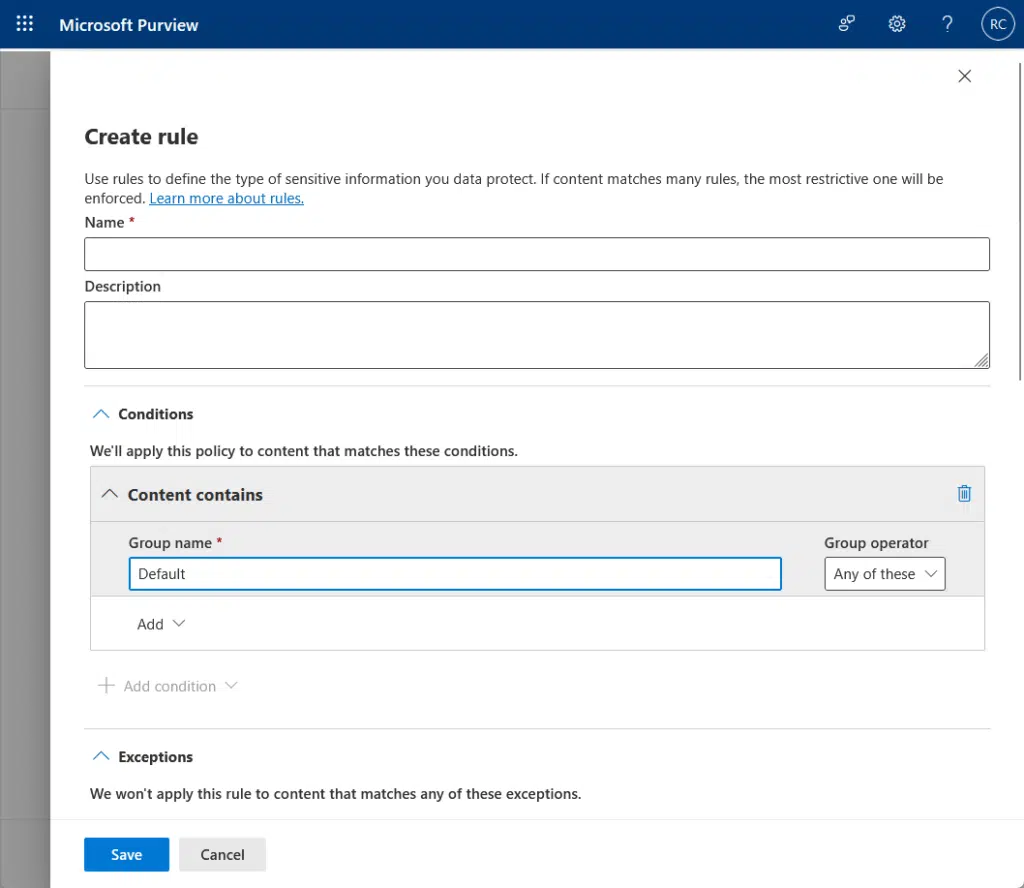
Depending on your needs, you may want to set up custom rules for more granular control.
This could include rules for specific types of data or data accessed by certain departments.
Step 3: Testing and implementation
Before fully implementing your DLP policies, it’s important to test them.
One reason is to ensure they work as intended without disrupting normal business operations.
Before finishing the setup, there is an option to run the policy in test mode:
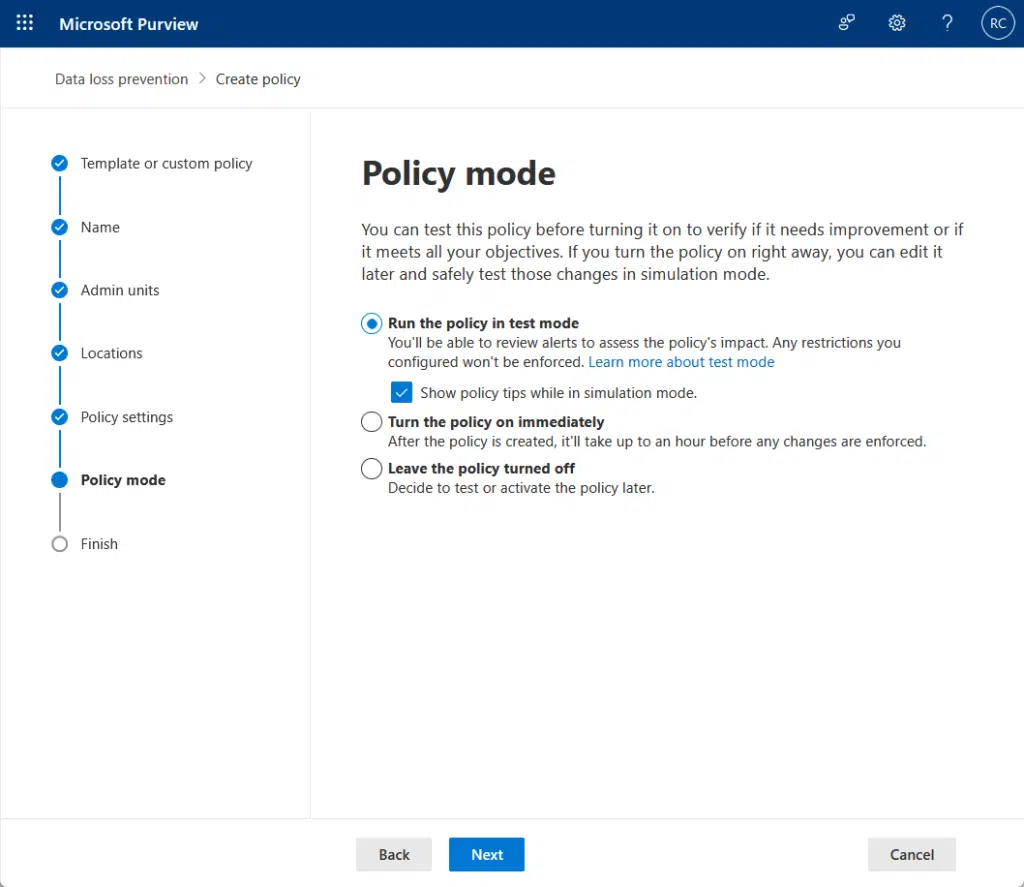
Finish the policy to run the test.
Don’t forget to do the following:
- Make sure to gather feedback from users.
- Adjust the policies based on that feedback.
Step 4: User education and training
I always tell people that the most effective policy is to teach users.
Likewise, the success of DLP policies is heavily dependent on user awareness and adherence.
There are at least two things you can do:
- Training sessions: Conduct training sessions for users to understand the importance of DLP and how to comply with the policies.
- Regular updates: Keep the users updated on any changes to the DLP policies and provide continuous education on best practices.
Advanced DLP Strategies
If your organization is looking to enhance the DLP measures beyond the basics, there are also advanced strategies.
These strategies usually involved third-party tools and customizing DLP to suit complex SharePoint environments.
Third-Party DLP Tools
While the built-in DLP features in SharePoint Online are great, third-party tools can provide more security and functionality.
Some advantages of using third-party DLP tools for SharePoint:
- Comprehensive coverage
- Advanced analytics and reporting
- Integration with other platforms
There are a lot of such tools available — but I’ll mention three:
1. Fortra Digital Guardian
Fortra is a comprehensive data protection platform for sensitive data and intellectual property.
It’s usable across corporate networks, endpoints, and apps, and is available as a SaaS or managed service deployment.
Do note that the Digital Guardian is part of Fortra’s cybersecurity portfolio.
Basic features:
- Immediate visibility: Provides immediate visibility into an organization’s assets for enterprise-wide data protection.
- Fast deployment: Offers quick startup and results, minimizing the time to protection.
- Cross-platform coverage: Protects data across various platforms, including Windows, macOS, and Linux.
- Comprehensive controls: Includes pre-built policies for data discovery, monitoring, logging, and blocking threats.
- Interoperability: Operates with existing data classification tools to enhance policy granularity and reduce false positives.
- Analytics & reporting: Empowers security teams with cloud-delivered data protection and reporting capabilities.
2. SolarWinds Access Rights Manager (ARM)
SolarWinds Access Rights Manager is made to automate user access policy, analysis, and enforcement.
It’s important for effective data loss prevention as it provides visibility into the following:
- Active Directory user provisioning and de-provisioning
- Azure AD user provisioning and de-provisioning
Basic features:
- Automated user access management: Implements automated tools for user provisioning and de-provisioning.
- Incident response acceleration: Sends alerts for suspicious activities to increase containment likelihood and protect sensitive information.
- Compliance reporting: Offers reporting capabilities to meet compliance and auditing requirements.
- Visibility and control: Provides critical visibility into Active Directory by monitoring and auditing changes.
- Integration: This can be fully integrated with other systems like CMDB and provisioning systems through an extensive API.
3. Symantec Data Loss Prevention
Symantec Data Loss Prevention (DLP) helps organizations understand how sensitive information is being used and handled.
It provides a comprehensive look into three vital elements:
- Discovery
- Monitoring
- Protection capabilities
The protection capabilities extend across various channels, including cloud, email, web, endpoints, and storage
Basic features:
- Data discovery: Discovers where data is stored across cloud, mobile, network, endpoint, and storage systems.
- Usage monitoring: Monitors how data is being used on and off the corporate network.
- Real-time protection: Protects data from exposure or theft in real-time.
- Comprehensive coverage: Offers broad data protection for various channels, including removable storage, desktop email, web apps, and cloud apps.
- Policy and incident management: Uses a single web-based console for defining data loss policies and managing incidents.
Monitoring and Maintaining DLP Measures
The truth is:
Effective DLP is not a set-and-forget solution — it requires ongoing monitoring and maintenance.
To maintain the effectiveness of the DLP, your organization has to implement strategies for continued assessment and improvement.
Techniques for Monitoring DLP Effectiveness
Here are techniques you can apply:
Regular Review of DLP Alerts and Logs
This one is kind of obvious — consistently reviewing alerts and logs related to DLP is a must.
Doing this will provide you with a deeper understanding of the incidents that occur within the system/environment.
Key actions include:
- Analyzing the frequency and types of alerts to identify patterns or recurring issues.
- Distinguishing between false positives and legitimate threats to fine-tune DLP configurations.
- Adjusting DLP rules based on the insights gained from log reviews to enhance accuracy and efficiency.
Performance Metrics
Like with all things important — metrics are important in assessing the impact of DLP policies on business operations.
But take note:
You and your organization must strike the right balance between security and operational efficiency.
Considerations involve:
- Monitoring how DLP policies affect workflow and employee productivity.
- Identifying any operational bottlenecks caused by DLP measures.
- Making necessary adjustments to DLP rules to minimize disruption without compromising security.
Compliance Audits
You also need regular compliance audits.
They will make sure that your data loss prevention measures align with data protection laws and regulations.
Essential steps include:
- Conducting thorough audits to review compliance with standards like GDPR, HIPAA, etc.
- Updating DLP policies to address any gaps or changes in legal requirements.
- Documenting compliance efforts to aid in any legal or regulatory reviews.
User Behavior Analysis
The key to a successful DLP is the users.
That’s because understanding user behavior helps in detecting potential security risks and ensuring the DLP’s effectiveness.
Important aspects to focus on:
- Identifying unusual patterns or behaviors that might indicate attempts to bypass DLP controls.
- Monitoring for unintentional misuse of data can be just as harmful as malicious actions.
- Using insights from behavior analysis to update training programs and user awareness initiatives.
Tips for Maintaining and Updating DLP Strategies Over Time
If you’ve read everything here, I actually explained some of them already.
But if not, here’s a rundown on how to maintain and update your DLP strategies:
1. Scheduled Policy Reviews
That’s right — you have to schedule policy reviews.
They help in ensuring that your data protection strategies stay relevant and effective.
This should include:
- Setting a fixed schedule for periodic reviews, such as quarterly or bi-annually.
- Adapting policies in response to significant changes in the IT environment, like new software deployments or system upgrades.
- Aligning DLP updates with changes in business operations or strategies to maintain data security consistency.
2. Stay Informed About Emerging Threats
No need to know it all or anything.
But keeping up-to-date with emerging cybersecurity threats helps maintain robust DLP strategies.
Key practices involve:
- Monitoring cybersecurity news and updates from trusted sources.
- Participating in industry forums and conferences to gain insights into new threat vectors.
- Regularly updating your DLP strategies to counteract these evolving threats effectively.
3. Training and Awareness Programs
As I implied in an earlier section, it’s important to teach users about data loss prevention.
At the very least, you need a continuously updating training and awareness program about the latest DLP policies.
Essential steps include:
- Regularly reviewing and updating training materials to reflect the latest DLP policies.
- Conducting frequent training sessions to ensure all employees are aware of their data protection responsibilities.
- Incorporating real-world examples and interactive elements to enhance learning and retention.
4. Leverage User Feedback
It’s sometimes difficult to know when a policy is hindering operation efficiency.
This is why encouraging and utilizing feedback from users is important for making user-centric improvements.
This can be achieved through:
- Creating channels for users to provide feedback on DLP policies and their impact on day-to-day work.
- Analyzing feedback to identify common challenges or areas needing clarification.
- Using these insights to refine DLP measures, making them more effective and user-friendly.
5. Technology Upgrades
Lastly, it’s not only the threats that evolved — the tools you can use also evolve.
This is why keeping up with technological advancements and getting upgrades can improve the DLP capabilities.
Considerations should include:
- Regularly assessing current DLP tools for their effectiveness and scalability.
- Exploring new technologies that offer improved data protection features.
- Evaluating and integrating tools that complement your existing DLP solutions.
The bottom line is that:
Monitoring and maintaining your DLP measure ensures that your SharePoint environment remains secure.
You need to take a proactive approach to safeguarding sensitive information in your organization.
If you have more questions about DLP strategies in SharePoint, feel free to leave a comment below.
For further inquiries or business concerns, kindly use the site’s contact form. I’ll make sure to reply promptly.

