Last Updated on April 4, 2025
Worried about your data in the cloud?
In this guide, I will give you an overview of SharePoint Online security and how it keeps your files and access safe.
Let’s get started.
Table of Contents:
Should you be worried?
Honestly, you don’t really need to be worried, but you should definitely stay aware. 👀
SharePoint Online has strong security built in, things like:
- Encryption
- Access control
- Compliance certifications
- Threat detection
Microsoft handles a lot on the backend to keep things locked down, but like any cloud service, it really depends on how it’s used.
If people in your org are sharing stuff carelessly or permissions aren’t managed well, that’s where issues can pop up.
So it’s less about the platform itself and more about how it’s configured and used.
Sign up for exclusive updates, tips, and strategies
Authentication and Access Control
These two are the backbone of SharePoint Online security as they decide who gets in and what they can do.
User Authentication Mechanisms
User authentication is all about verifying that someone is who they say they are before giving them access.
It’s built on top of Microsoft Entra ID (previously Azure AD), which handles logins for all Microsoft 365 apps.

Basically, when someone tries to sign in, Entra ID checks their username and password.
But passwords alone aren’t enough anymore, and that’s where MFA (Multi-Factor Authentication) comes in.
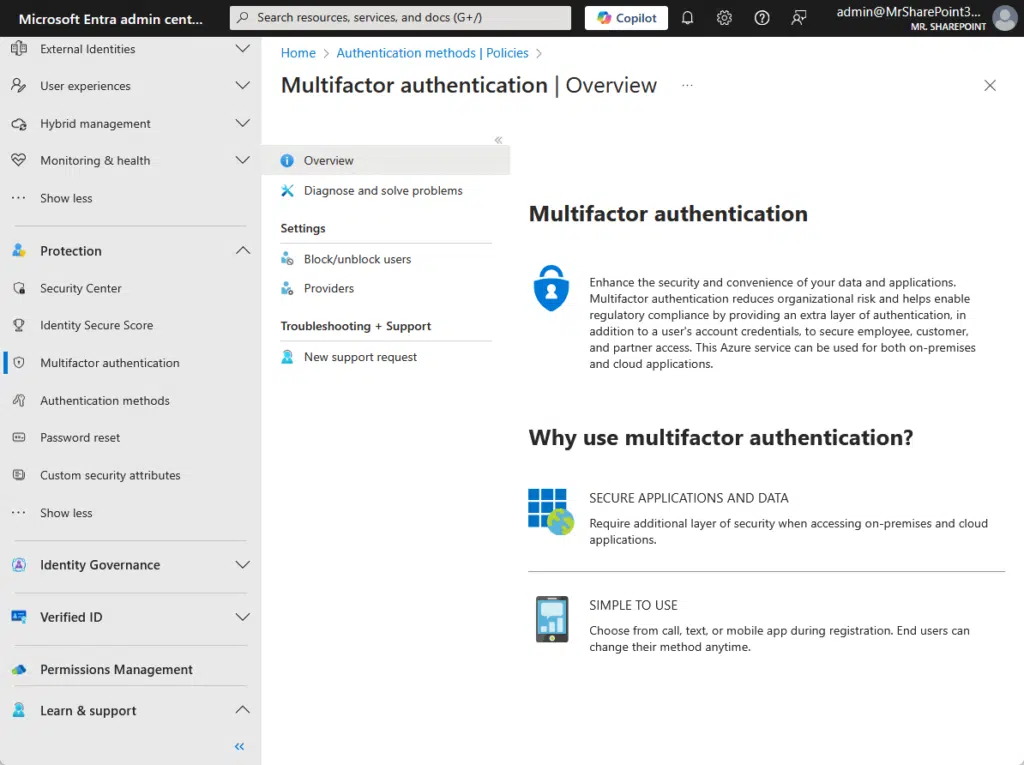
MFA adds an extra step to the login process.
Users might need to enter a code from an app, respond to a push notification, or use a fingerprint or face scan.
Here’s an example:

What’s nice, though, is that Microsoft implements security defaults in Microsoft Entra ID, requiring users to use MFA.
The cool part here is that even if someone’s password is stolen, that second factor keeps the account protected.
You can also implement conditional access policies here to control how and when users can access apps like SharePoint.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is how you manage who can do what.
It’s a way to organize permissions based on roles instead of assigning them by user, which would be a nightmare. 😥
There are 2 components here you need to be aware of:
- Roles and permissions
- Groups
A role is like a label (like editor) that comes with a set of permissions, while permissions control actions (like deleting content).
You assign the role, and the user gets those abilities.
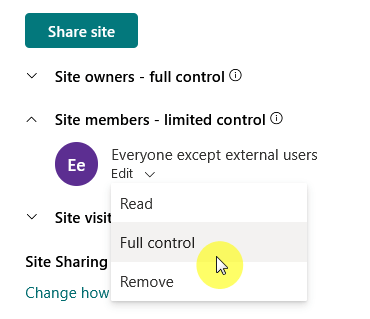
The second part is groups.
Basically, instead of assigning roles to users one at a time, you create groups (like “Marketing Team”) and assign the role to the group.
Everyone in the group gets the same permissions, which makes it way easier to manage and change things.
So RBAC = define roles → assign to groups or users → control access.
It keeps things organized and scalable; if someone changes departments, you just move them to a different group.
No need to redo their permissions from scratch. 🙂
Data Protection Measures
The principle is that data security is all about keeping your files safe, whether they’re being stored or shared.
Encryption
Encryption is basically the process of scrambling data so no one can read it unless they have the key.
There are 2 types of encryption in SPO:
- At rest
- In transit
Basically:
| Aspect | Encryption at Rest | Encryption in Transit |
| When It Happens | After the data is stored in SharePoint | While data is being sent or received |
| What It Protects | Files sitting in cloud storage | Files moving between user devices and SharePoint |
| How It’s Done | Uses BitLocker and per-file encryption | Uses TLS (Transport Layer Security) |
Both types work together.
At rest handles the storage side, and in transit handles the travel, from upload to storage to download, data stays locked down.
You won’t see this happening, but a good indication is if the site URL starts with https:// like this:
https://mrsharepoint365.sharepoint.com/sites/TeamSite
If you see that, you’re already using TLS encryption in transit as that little padlock in your browser bar means your connection is encrypted.
Information Rights Management (IRM)
IRM is like giving files their own built-in security rules, even after they leave the SharePoint environment.
It works by restricting what users can do with files, like stopping them from printing, copying, or forwarding content.
Here’s how it applies restrictions:
- If IRM is turned on for a library or list, every file downloaded from there gets those restrictions baked in.
- For example, you can stop people from printing a Word doc or prevent screenshots in Excel.
- Even if someone saves the file to their desktop, those rules still apply.
That’s the beauty of IRM—it travels with the file.
To use it, you will need to activate the Rights Management Services first in the Microsoft 365 admin center, then enable IRM in SPO.
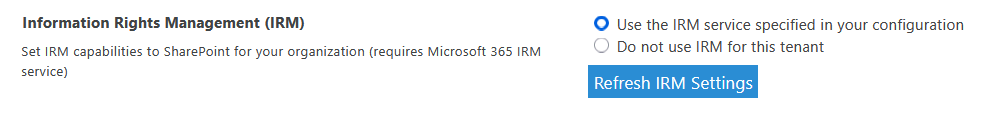
But take note that IRM is considered a premium feature and requires specific licenses to use in SharePoint Online.
If your current plan doesn’t include AIP, you would need to purchase it separately to use IRM features in SharePoint Online.
Data Loss Prevention (DLP)
DLP is a feature that helps stop sensitive information from getting out by accident.
You can create these policies in the Microsoft Purview compliance portal through built-in templates to detect things like:
- Bank info
- Social security number
- Passport data
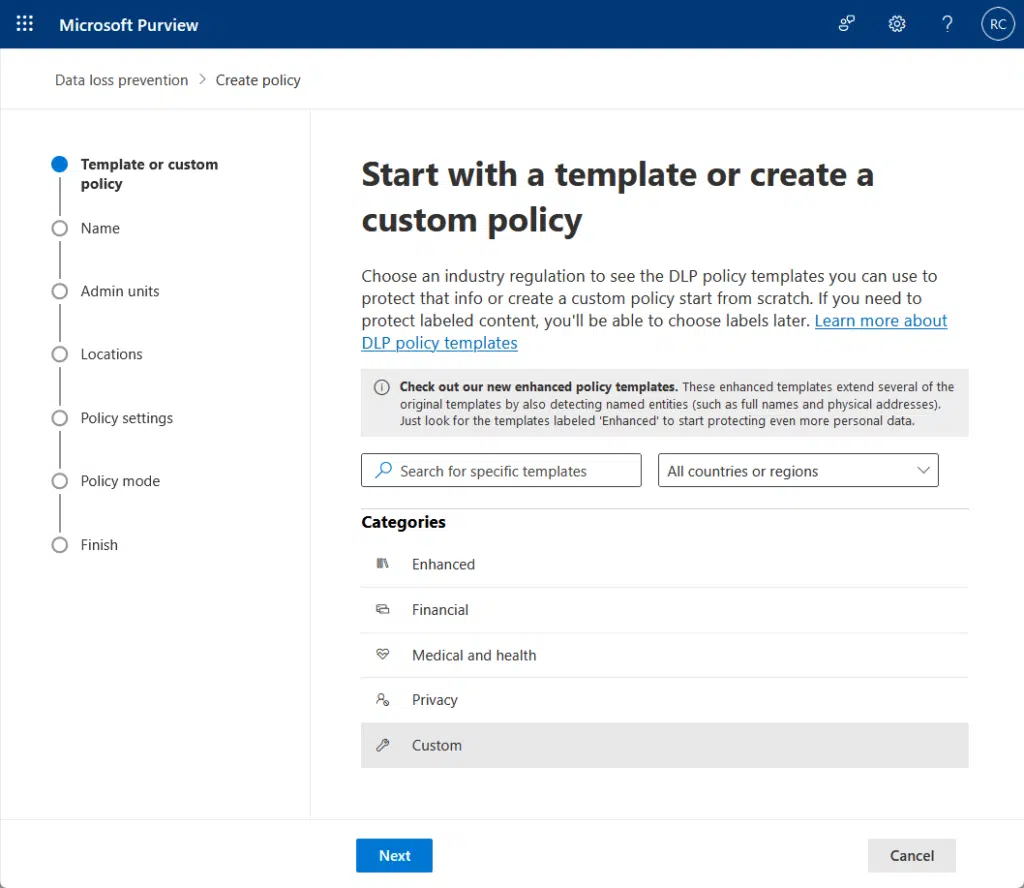
If it finds something, it can automatically block access, show a warning, or send alerts to admins, depending on your settings.
This works the moment someone uploads or shares a document, not afterward.
What’s nice is that it doesn’t just apply to SharePoint; it also covers OneDrive, Teams, and Exchange.
For example, you might block sharing outside the company if a file contains credit card numbers.
It’s great for staying compliant with laws like GDPR and for avoiding costly mistakes like sending the wrong file to the wrong person.
External Sharing and Collaboration
External sharing and collaboration let people outside your organization access content, without losing control over it.
Configuring External Sharing Settings
This is basically where you decide how open or locked down your SharePoint is when it comes to outsiders.
External sharing settings control whether people outside your company can access your content, and how they do it.
When setting the external sharing for the whole tenant and a site, there are two “permissive” options:
- Anyone
- New and existing guests
These can be done in the SharePoint admin center.

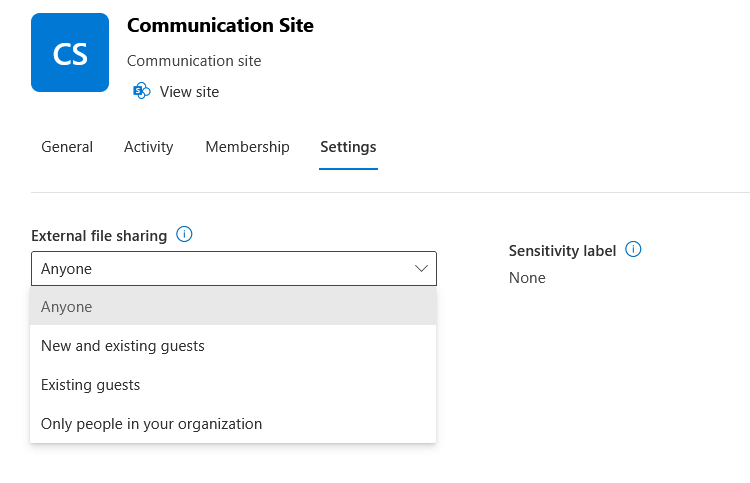
Personally, I recommend you set this up for new and existing guests so you can track who has access to what.
Shareable links also have these security settings where you can make the link work for anyone or people with existing access.
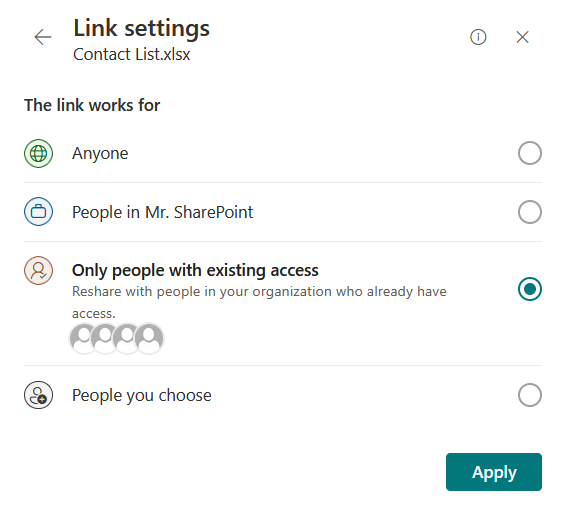
Anonymous links let you share with anyone who has the link, no sign-in required, and you won’t know who they are.
Authenticated external users need to sign in using a Microsoft account or another trusted login and you can track what they do.
Another handy feature is expiration dates, where you can set a time limit, like 7 days, for how long someone can access the file.
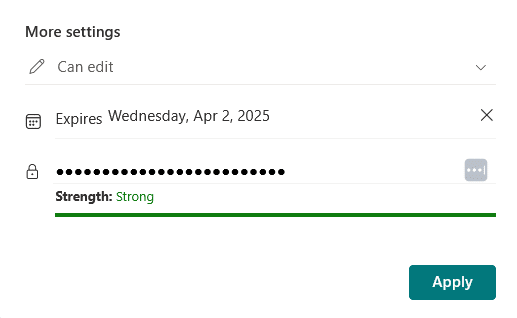
After that, the link just stops working, stopping things from being shared forever, especially if it’s sensitive or time-based info.
In short, configuring these settings gives you control over who gets in, how they get in, and for how long.
It’s a good balance between ease of sharing and staying safe. 👍
Managing Guest Access
Managing guest access is about giving the right people access to your SharePoint content, without opening the door too wide.
Granting guest access means inviting someone outside your organization, like a vendor or client, to view or work on files.
You can do this for a whole site by simply sharing it:
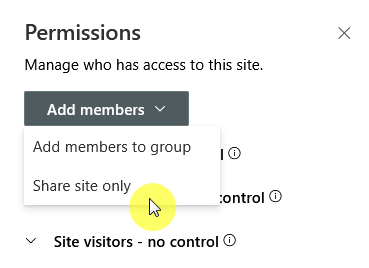
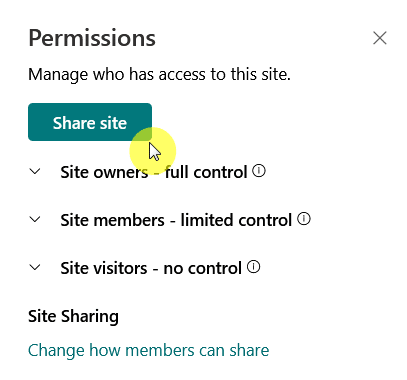
This also happens automatically when you send a sharing link that requires sign-in; once they accept, they become a “guest”.
Because of this, monitoring guest permissions is key, as you want to regularly check what guests have access to.
If you want to make this easier, you can use Microsoft 365 Groups, which work across SharePoint, Teams, Outlook, and more.
If you add a guest to a group, they get access to all the connected tools: the SharePoint site, team chats, calendars, etc.
It’s a clean way to manage everything in one spot, especially when collaborating with the same external team on multiple things.
Compliance and Auditing
These two help make sure your data handling meets legal, industry, and internal standards, and that you can prove it if needed.
Compliance Standards
SharePoint Online is built to meet a lot of the big compliance standards out there.
Microsoft has designed it with security, privacy, and data control in mind, so companies can trust it even in regulated industries.
Here’s a quick rundown:
| Standard | What It Covers | How SharePoint Online Supports It |
| GDPR (General Data Protection Regulation) | Data privacy and protection for individuals in the EU. | Provides tools for data access, deletion, and management to help organizations meet GDPR requirements. |
| HIPAA (Health Insurance Portability and Accountability Act) | Protection of sensitive patient health information in the U.S. | Offers capabilities to support HIPAA compliance, including data encryption and access controls. |
| ISO 27001 | International standards for information security management. | Certified for ISO 27001, demonstrating adherence to rigorous information security practices. |
| ISO 27018 | Code of practice for protecting personal data in the cloud. | Complies with ISO 27018, ensuring protection of personal data processed in the cloud. |
| FedRAMP (Federal Risk and Authorization Management Program) | Standardized approach to security assessment for cloud products and services used by U.S. federal agencies. | Meets FedRAMP requirements, allowing use by U.S. government agencies. |
| SOC 1, SOC 2, SOC 3 (Service Organization Control reports) | Frameworks for managing and reporting on controls related to financial reporting, security, and privacy. | Undergoes regular audits to produce SOC reports, providing transparency into security and compliance practices. |
| CSA-STAR (Cloud Security Alliance Security, Trust & Assurance Registry) | Certification for cloud security based on CSA best practices. | Achieves CSA-STAR certification, indicating robust cloud security measures. |
| ISO 22301 | International standard for business continuity management. | Aligns with ISO 22301 to ensure preparedness for disruptive incidents. |
| ISO 20000-1 | Standard for IT service management systems. | Adheres to ISO 20000-1, demonstrating effective IT service management practices. |
These certifications and support tools don’t automatically make your organization compliant, but they give you a strong foundation.
You still need to configure things right, like setting SharePoint permissions and retention policies to meet the actual rules.
So it’s a shared responsibility: Microsoft secures the platform, and you manage how it’s used.
Auditing and Monitoring
These let you keep an eye on what’s happening with your content, who’s accessing what, when, and what they’re doing with it.
Audit logs are your go-to tool for this, you can turn them on in the Microsoft Purview compliance center.
Once enabled, these logs record user actions like:
- Viewing or editing documents
- Sharing files or folders
- Deleting items
- Accessing content from outside your organization
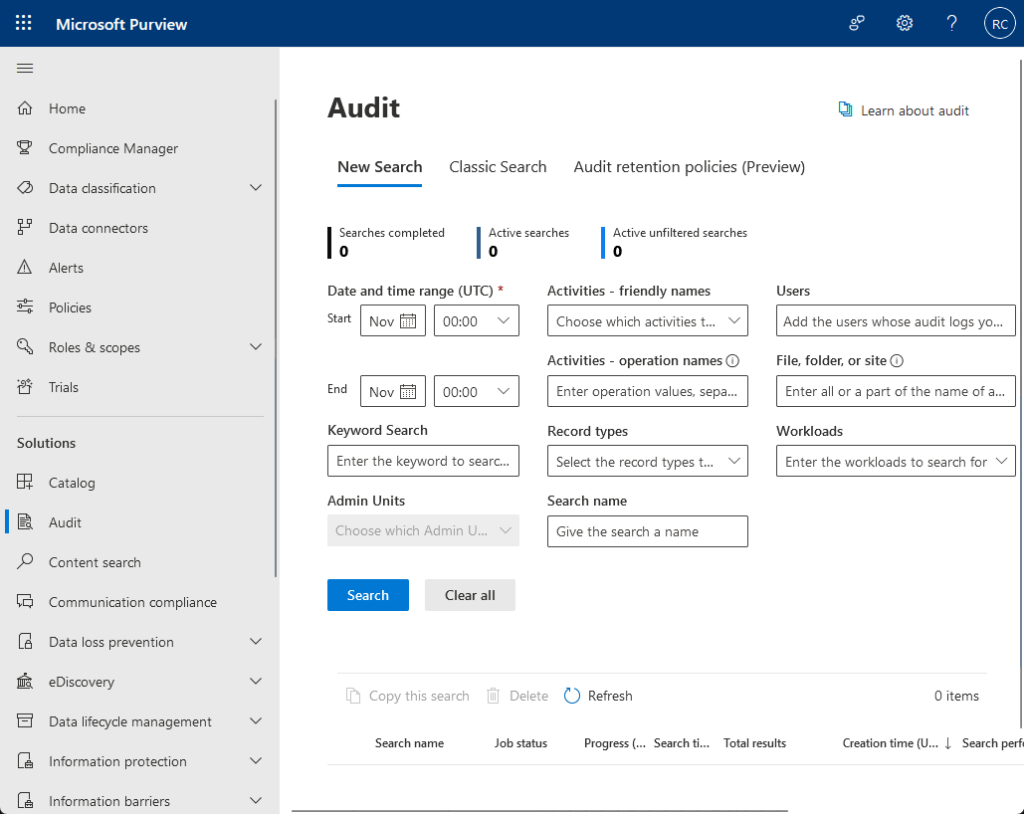
Admins can search the logs by user, date range, or activity type.
It’s super useful if you need to investigate something later, like “Who deleted that folder?” or “Was this file shared externally?”
Alerts for suspicious activities take things a step further, you can set up policies that watch for risky behavior, like:
- Mass downloads in a short time
- Unusual login locations
- Sharing sensitive data outside the org
When these things happen, admins can get an email alert, so they can jump in quickly.
These tools don’t just help with security, they also help with compliance, since you can show a full trail of actions if needed.
It’s like having a SharePoint security camera for your files. 🎥
Do you have any questions about this SharePoint Online security overview? Let me know below.
For any business-related queries or concerns, contact me through the contact form. I always reply. 🙂

