Last Updated on December 14, 2023
Confused about these two groups?
In this guide, you will learn the differences between SharePoint groups and Active Directory groups, their pros and cons, use cases, and more.
Let’s get started.
Table of Contents:
Definition and Key Features
Both groups are essential tools to effectively manage permissions in SharePoint.
Especially when dealing with a SharePoint site collection or even multiple SharePoint site collections.
Basically, SharePoint groups are collections of users that are created within SharePoint to manage permissions and access to SharePoint sites and resources.
These groups work in SharePoint groups exclusively.
Here are its key features:
- User management: Easily add or remove users from a SharePoint site
- Permission levels: Assign different permission levels like read, contribute, and full control
- Integration with Microsoft 365: Seamlessly integrate with other Microsoft 365 services like Teams and OneDrive
In terms of pros and cons:
| Pros | Explanation | Cons | Explanation |
| Ease of Use | Quick setup without needing advanced IT skills | Limited to SharePoint | These groups are specific to SharePoint and don’t extend to other services |
| Fine-Grained Permissions | Allows for detailed control over what users can see and do | Lack of Advanced Features | Doesn’t offer as many advanced features as Active Directory Groups |
| Collaboration Features | Built for team collaboration with features like shared calendars and task lists |
What are Active Directory Groups?
Active Directory groups are collections of user accounts, computers, and other groups that are managed centrally within the Active Directory service.
If you’re not familiar with the service, it’s a directory service developed by Microsoft for Windows domain networks.
It’s a centralized system that automates network management of user data, security, and distributed resources.
The service allows administrators to manage policies and deploy software.
Here are the key features of Active Directory groups:
- Centralized management: Manage all users and permissions from a single location
- Group types: Offers different types of groups like Security Groups and Distribution Groups
- Scalability: Designed to scale with your organization, accommodating thousands of users
In terms of pros and cons:
| Pros | Explanation | Cons | Explanation |
| Comprehensive Control | Centralized control over network resources | Complexity | Requires a deeper understanding of IT concepts |
| Advanced Features | Offers functionalities like nested groups and group policies | Cost | Can be more expensive to set up and maintain |
| High Scalability | Ideal for large organizations with complex needs |
Sign up for exclusive updates, tips, and strategies
Creation and Management
Managing user access and permissions is a critical aspect of any organization’s IT strategy.
Whether you’re a small business or a SharePoint site owner:
Understanding how to create and manage SharePoint groups and AD groups can significantly impact your workflow and security.
Naturally, you need to be able to access the SharePoint site settings page to do this.
From the home page of the site:
- Click the gear icon
- Select site permissions
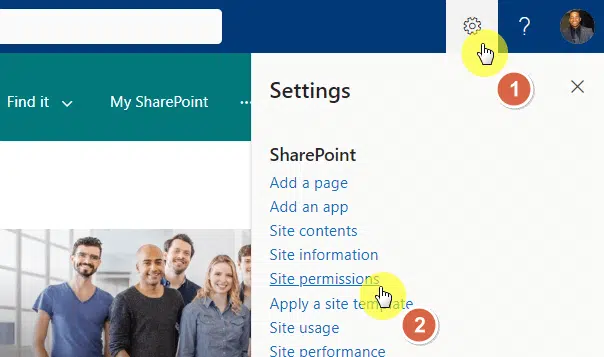
You will then see basic site permission settings here.
Click the advanced permissions settings link near the bottom of the panel:
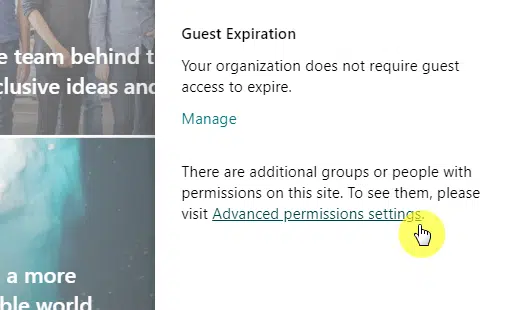
The actions above will bring you to a classic-looking permissions page in SharePoint.
What you need to do here is click the create group button from the toolbar:
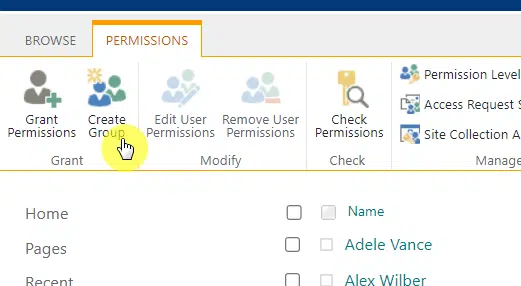
This will open another page where you have to complete the details/information of the new group.
Complete that, along with the group permission you want to give to the group.
Click the create button after you’re done:
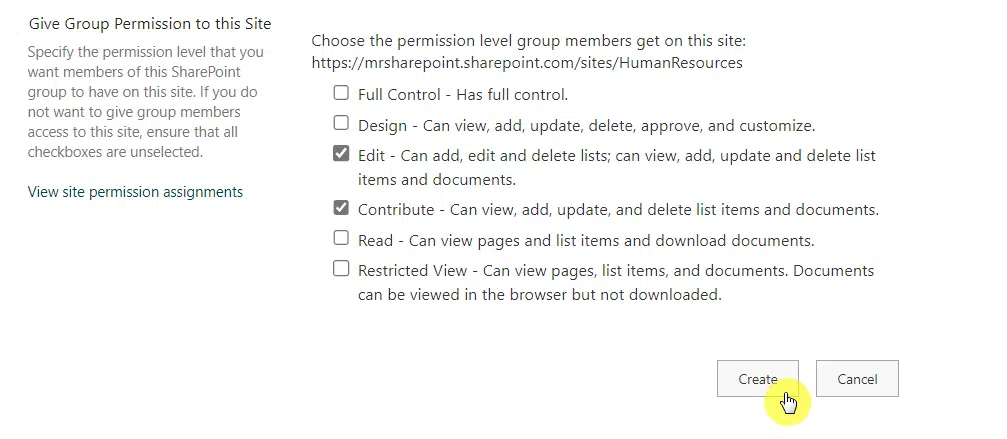
Step #3: Manage the group
There are a lot of things you can do in the group — starting with adding more members to the Sharepoint group.
From the list of groups, you need to click the name of the group you want to manage the membership:
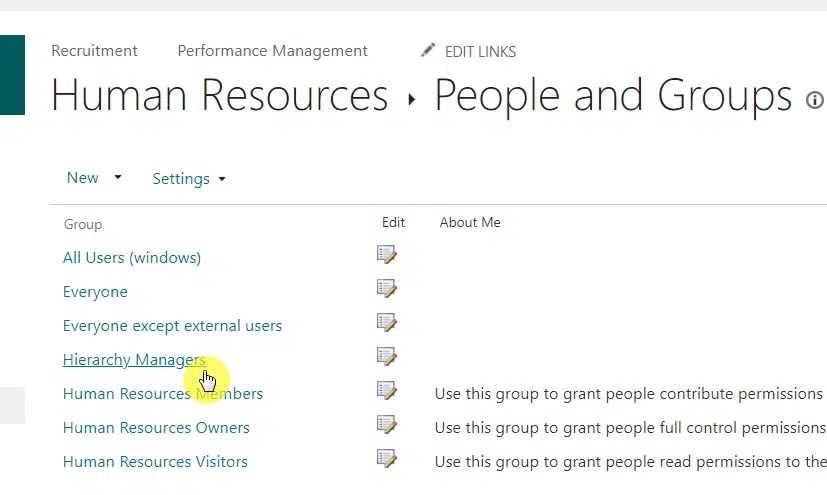
If you want to add a new member, just click new > add users to this group.
This will open a window where you can add a user to the group membership.
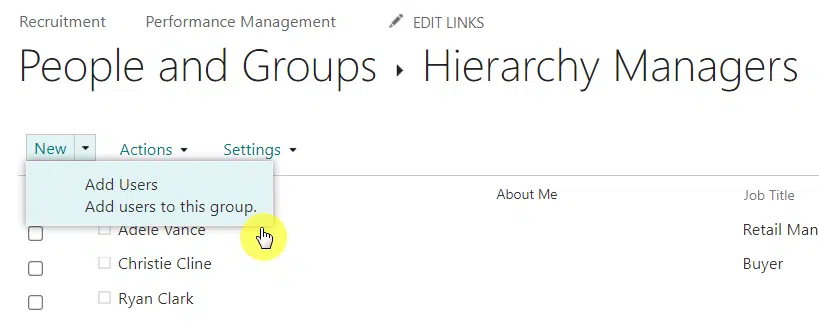
If you want to remove the user:
- Click the user’s box to select it
- Go to actions > remove users from group
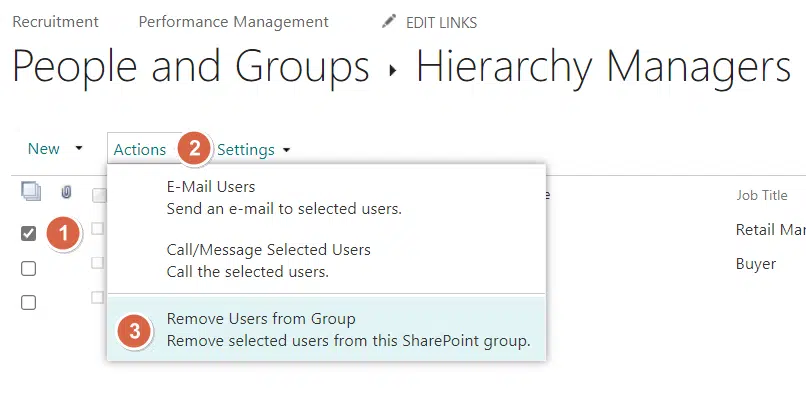
For changing the group settings:
- Click the settings button
- Choose what you want to manage

For example, the group settings contain the option to delete the group.
The whole page looks like this:
Related: Beginner’s Guide to SharePoint Security Groups (Overview)
Creating and Managing Active Directory Groups
Not everyone can create and manage AD groups.
Maintaining AD groups typically falls under the responsibilities of IT experts who are part of the traditional on-premises AD service.
These AD groups control access to various resources and services.
But normally, the process of creating an AD group is as follows:
- Accessing the tool from the server where AD is installed
- Go to the folder where you want to create the group
- Fill in the group name, choose the group type, and set the scope
As for user management, it’s similar to a SharePoint group.
You can:
- Add users
- Remove users
- Apply group policies
AD group membership is a critical aspect that needs to be managed carefully, especially when dealing with AD security groups.
AD groups are different from Azure AD groups, although they are closely related and often used in conjunction to manage identities and resources.
If you’re confused between the two, here are their key differences:
- Location: Active Directory is typically on-premises, while Azure AD is cloud-based.
- Integration: Azure AD is designed to integrate easily with modern cloud services, while traditional AD is geared more towards on-premises applications.
- Management features: Azure AD includes features more aligned with cloud management, such as device compliance checks, which are not native to traditional Active Directory.
Permissions and Security
Security is a top priority for any organization.
The way you manage permissions can either make your system impenetrable or leave it vulnerable.
Let’s get into how SharePoint Groups and Active Directory Groups handle permissions and security.
There are six default permission levels in a SharePoint group:
- Full control: Allows users to view, add, delete, or modify all content, settings, permissions, and design elements
- Design: Users can view, add, delete, or modify items, documents, and the site’s structure or design.
- Contribute: Users can add, edit, and delete items in lists and libraries but cannot modify the site’s design
- Read: Enables users to view content but not add, edit, or delete it
- Limited access: Grants access to specific lists, libraries, items, or documents without site-wide access
- View only: Allow users to read content but not download documents
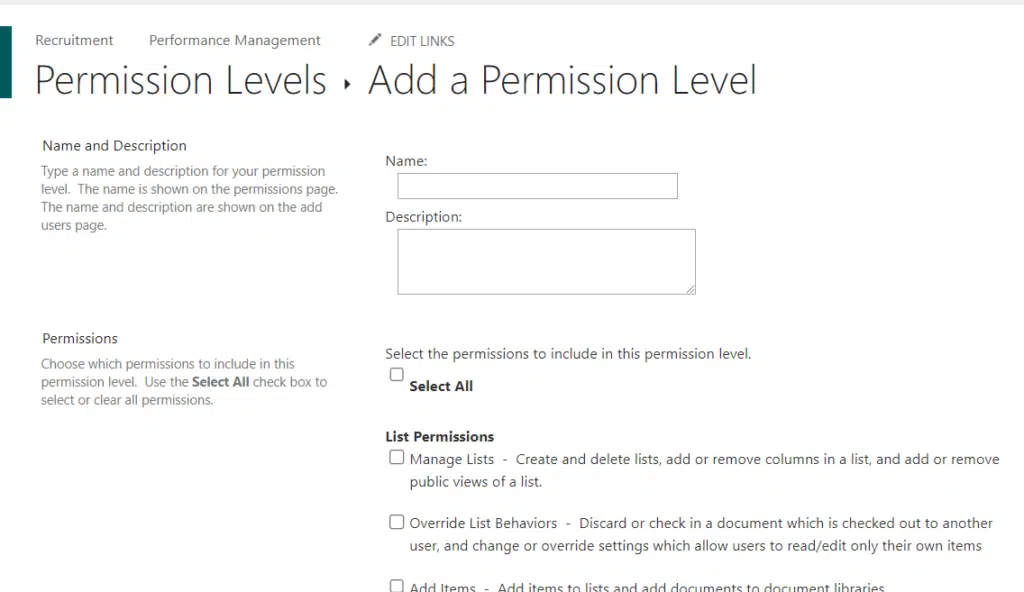
However, you can also create a custom permission level in SharePoint.
If you go back to the advanced permission settings, you can see a permission levels button from the toolbar:
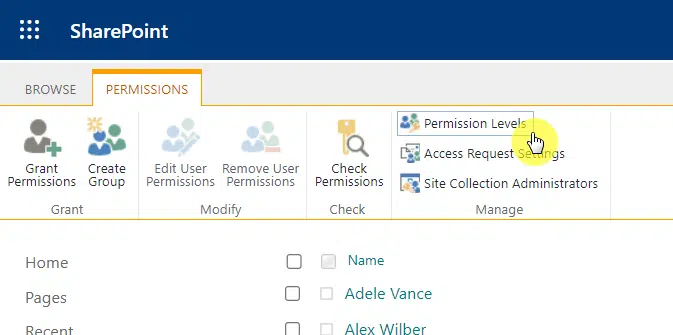
As expected, you will see here all the permission levels.
You can then click on the add a permission level button:
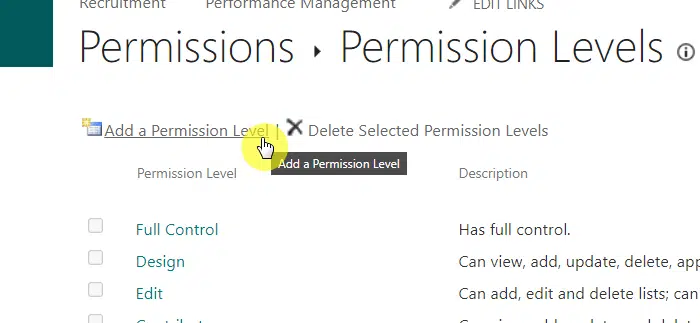
From there, you will be able to adjust the permission level according to your needs.
The next page looks like this:
Related: How to Create a SharePoint Custom Permission Level (Guide)
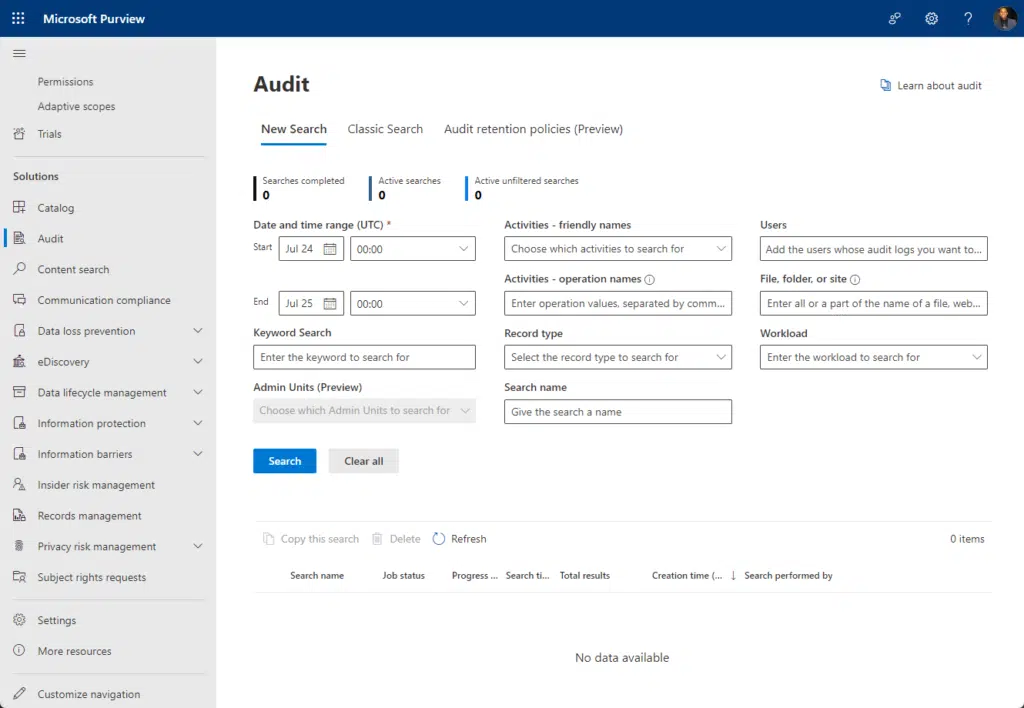
Another security measure is audit logs, where you can track user activities for compliance and security monitoring.
You can view it in the Microsoft Purview under the audit solution:
Related: Risks and Vulnerabilities: Is SharePoint Secure? (Updated)
Active Directory Groups
AD groups are a little complicated.
But in essence, there are admins when it comes to user rights:
- Service administrators: Overseeing and managing the Active Directory Domain Services (AD DS) — includes the setup and control of domain controllers and the configuration of AD DS
- Data administrators: Safeguarding the information in AD DS, as well as ensuring the integrity of data on servers and client machines that are part of the domain
For security groups:
- Security groups: Serve the purpose of defining access rules for common assets
- Distribution groups: Utilized to assemble lists for distributing emails
Rights for specific users can be pre-set in some security groups at the time of Active Directory installation.
Group policies can be leveraged to allocate particular responsibilities to security groups.
When it comes to assigning permissions:
- Permissions stand apart from user rights and are specified for a security group to regulate access to a communal resource.
- Permissions specify not only who may interact with the resource but also to what extent, such as having Full Control or just Read access.
Flexibility and Customization
Flexibility and customization are not just nice-to-haves — they’re essential.
Both SharePoint Groups and Active Directory Groups offer varying degrees of flexibility.
For instance, the governance model shifts control according to the type of group you are using.
Flexibility
- User management: Easily add or take away people from a SharePoint Group without messing up the existing rules for who can see or do what
- Nested groups: Put groups inside other groups (helps you manage who can do what in a more organized way)
- Site-specific groups: Each SharePoint site can have its own groups (lets you control who can do what on each individual site)
- Dynamic membership: Automatically add people to groups based on certain things like their job title (not as advanced as Active Directory)
Customization
- Custom permission levels: Make your own sets of rules for what people in a group can do
- Group settings: Change the settings for each group, like who can see the group’s members or who can change the group’s settings
- Custom workflows: Set up automatic actions that happen when certain things occur, like adding someone to a group when they join a project
- Personalized content: Show different content to different groups of people, making the site more useful for everyone
Here are the pros and cons of the flexibility and customization in SharePoint groups:
| Pros | Cons |
| Highly customizable permission levels allow for tailored security measures | Customization can become complex and hard to manage |
| Flexibility in user and group management saves time and effort | Too much flexibility can lead to security loopholes if not managed carefully |
| Site-specific groups provide granular control | May require additional governance to keep site-specific groups in check |
| Integration with custom workflows for automated management | Custom workflows require proper setup and maintenance |
Flexibility and Customization in Active Directory Groups
Flexibility
- Update automatically: Dynamic Groups in Active Directory change their members on their own based on things like job role or location
- Include other groups: Put groups inside other groups in Active Directory, making it easier to manage a big organization
- Span across domains: Create groups that work across different parts of your organization, even if they’re not in the same domain
- Choose group types: Pick between Security Groups for setting permissions and Distribution Groups for sending emails
Customization
- Add custom features: Add your own attributes in Active Directory to make dynamic groups even more tailored to your needs
- Set rules: Use Group Policy to enforce specific rules or settings across your organization
- Delegate tasks: Let other users or groups handle some admin tasks while still keeping overall control
- Automate actions: Use scripting languages like PowerShell to make some tasks happen automatically
Here are the pros and cons of the flexibility and customization in established AD groups:
| Pros | Cons |
| Dynamic groups automate the process of adding or removing users, saving administrative time | Dynamic groups can become complex and require careful planning and testing |
| Nested groups provide a way to manage complex organizational structures efficiently | Incorrect nesting can lead to circular nesting errors and security issues |
| Group Policies offer robust customization options for security and configurations | Incorrect Group Policy settings can lead to system-wide issues |
| Delegation of control allows for distributed administration | Delegation requires a deep understanding of permissions to avoid security risks |
Examples of Use Cases
The use cases of each group can overlap depending on the category.
Below is a table that explains each use case category and how each group can help:
| Use Case Category | SharePoint Groups Use Case | How SharePoint Helps | Active Directory Groups Use Case | How Active Directory Helps |
| Access Control | Project Collaboration | Create project-specific groups for team collaboration on a centralized site | Access Control for Shared Resources | Create a Security Group for specific teams to control access to network drives |
| Departmental Needs | Departmental Sites | Create department-specific groups and sites with customized permissions | Software Deployment | Create a Security Group for specific computers to deploy software via Group Policy |
| External Collaboration | External Collaboration | Create groups with custom permissions for external stakeholders | Email Distribution | Create a Distribution Group for company-wide email announcements |
| Event Management | Event Planning | Use custom workflows in SharePoint Groups for event coordination | Multi-level Security | Use nested Security Groups to control access to sensitive data |
| Compliance | Compliance and Auditing | Create groups with strict permissions and auditing for compliance | Cross-Departmental Projects | Create a Security Group for cross-departmental access to shared resources |
| Knowledge Management | Knowledge Base | Create a ‘Read-Only’ group for a company knowledge base | Remote Work Configuration | Create a Security Group to enforce security settings and grant VPN access to remote workers |
| Administrative Delegation | N/A | N/A | Delegating Administrative Tasks | Create a Security Group to enforce security settings and grant VPN access to remote workers |
Do you have any questions on SharePoint groups vs. Active Directory groups? If yes, comment them down.
For any business-related questions/messages, send your query through the contact form here. I’ll reply asap.

