Last Updated on August 26, 2023
What can you do against the security risks in Microsoft Teams?
In this guide, I will share Microsoft Teams security best practices that you can implement and safeguard your data and organization.
Let’s get started
Table of Contents:
What are the security risks in Microsoft Teams?
Microsoft Teams is a great tool that became a hallmark in communication and collaboration within an organization.
But is Microsoft Teams secure?
Well, like everything else, it’s not perfect. Its not-so-exclusive nature makes it a target for a number of security risks.
Note: If you need a more thorough guide on the basics, read this tutorial: Microsoft Teams Tutorial: Become a Teams Expert Quickly.
Here are a few of them that can become Microsoft Teams security threats:
1. External users
The ability to provide guest access to external users is one of the reasons why so many organizations use Microsoft Teams.
That’s because guest users are normal people outside the company and are usually on a contract basis.
Since you don’t have to buy these people any special licenses, this saves organizations tons of money (while still having the external user use Teams).
On the downside, this feature presents potential problems as there are no restrictions whatsoever that govern which people can get this privilege.
By default, guests have permission to everything (by default) in Teams except for the following:
- Create meetings
- Access schedules
- Invite other guests
- Create teams
- Public team discovery
If you and your users aren’t careful enough, there is a risk that guest users would see sensitive data or content in Teams.
Note: For more info on adding external users, see this guide: How to Add External Users to Microsoft Teams.
2. Third-party apps
Another great thing about Microsoft Teams is that there are apps that can extend the capabilities of the platform.
Many of these apps allow you to access other platforms and use tools natively without leaving Teams at all.
For example, there are project management apps for Teams you can install like Asana, Trello, and Monday.com.
For these apps to work, they often require access to personal information and to the Teams app as well.
For example, GitHub requires permission to:
- Receive messages and data
- Access to profile information
- Send messages and notifications in a channel, chat, or meeting
- Access information from this team, chat, or meeting
Now, most apps like GitHub, Asana, and Trello are all trustworthy.
However, the fact that apps require permission to access data can lead to MS Teams security risks.
3. Open permissions model
By design, Microsoft Teams has an open-permissions model to allow for a smoother collaboration between team members.
Through this model:
- Users can create a team and make themselves the team owner
- Private channels without an owner can have any user as the new channel owner
- Team members have full, direct access to data within the public channels
- Guests, as I discussed earlier, also have permission except for a few things
In the case of channels without an owner, any member can potentially become the new owner.
Unfortunately, he/she can invite someone into the channel with that user viewing confidential content.
4. Information leakage
There are four primary concerns here:
- Users can unknowingly or deliberately share confidential content with other people.
- External users can view confidential content in the chat.
- External participants can give or request control of content via desktop control (when enabled).
- Though there’s a lower chance, malware can potentially catch confidential files in transit.
Any of these four can risk the company its intellectual property and reputation.
Note: For more info on desktop control in Teams, check out this guide: How to Enable External Control in Microsoft Teams.
In addition, team owners can change the privacy of their team quite easily:
This can pose a few risks especially if there is no one that manages the team owners as they can invite someone with malicious intent into the team.
5. Data management
Did you know that you can also set up a data retention policy in Teams?
Although that seems to be the case, the open permissions model sometimes becomes a hindrance to this policy.
That’s because the content in Teams is so dispersed and can easily spread from different teams and channels.
Many of the items you have read earlier can run counter to MS Teams best practices in data retention and data lifecycle management.
Note: I have talked more about Teams retention in this guide: The Definitive Guide: How to Manage Microsoft Teams Sprawl.
Sign up for exclusive updates, tips, and strategies
Microsoft Teams security best practices
Here are some Teams security best practices that you can implement:
1. Define Microsoft Teams governance
The first action you can take to implement great Microsoft Teams security is to create your own company MS Teams (automated) governance policies.
At the very least, your policies should include matters like:
- Who can create teams
- What content can users share (and where)
- How users should use Teams
- What to do when the team doesn’t have an owner
Note: For starters, you can read this guide: Microsoft Teams Best Practices Guide: Focus and Management.
A good example of this is creating a security group specifically for people with team creation capabilities. Unfortunately, this may affect other apps as well.
You can also use dynamic membership so that the system will automatically add or remove users from groups depending on their attributes.
2. Identify sensitive data
How can you protect sensitive data if users don’t have a clear definition of what composes sensitive data?
This is why identifying sensitive information is the second step I recommend since you need it if you want to protect sensitive information.
For this, you can create a data classification scheme by considering the following:
- What information do you deem important to keep?
- Where can you find that information?
- Who can access that information? (Or what kind of users can access that information)
- How do you use sensitive information or data?
- What level of protection do those data need?
If the kind of information you want to protect isn’t too classified, you could use a more relaxed approach to protecting your data.
Remember that users are vital to this approach since they are the ones who deal with data on a daily basis.
You need to educate them and make them part of the process of identifying and protecting confidential data in Teams.
Related: How to Create Sensitivity Labels in Microsoft 365
3. Set up app management
Since it’s likely that you would be using apps in your Microsoft Teams, then it’s important that you at least know how to manage them.
In Teams, there are three kinds of apps:
- Apps made by Microsoft
- Third-party apps
- Apps built by internal teams
The safest of these apps are those made by Microsoft and those developed by your internal teams. Third-party apps need more careful assessment.
Fortunately, there’s an easy way to restrict the use of apps depending on who made them.
For this, you need to be in the Microsoft Teams admin center > Teams apps > Manage apps > Org-wide app settings:
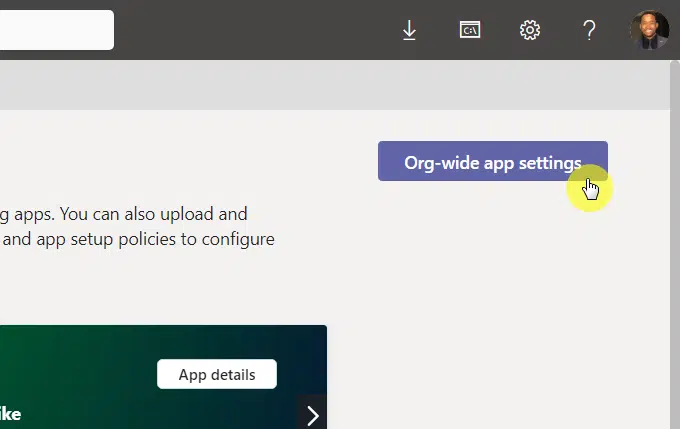
If you want a more granular control, you can find individual apps in the list on the same page in the admin center.
4. Use data security features
Microsoft 365 has built-in data security features to help companies safeguard their confidential data.
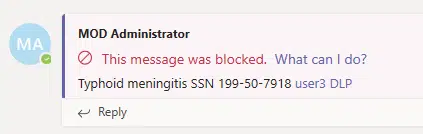
One of those features is data loss prevention, which basically prevents users from sharing sensitive data in a channel or chat.
For example, if a user mentions something that triggers this feature, this notification will pop out and blocks the message:
Not only does it apply to chat messages. it also applies to documents.
For example, if you send a document containing sensitive info to external users, this notification will pop out:
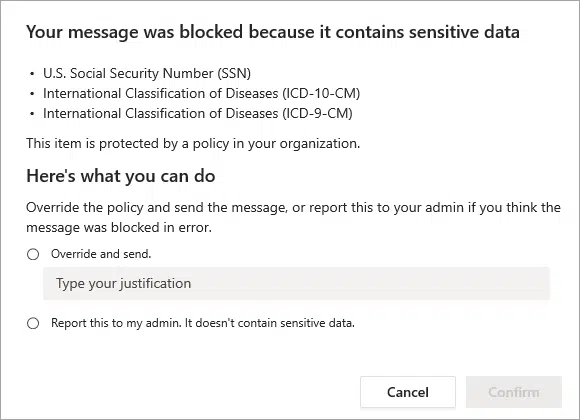
You can find data loss prevention in the compliance center. You can also go directly to this link to see if you have existing policies:
https://compliance.microsoft.com/datalossprevention?viewid=overview
Another feature is sensitivity labels, which lets you identify and protect your organization’s data through encryption.
In a nutshell, sensitivity labels allow you to:
- Apply a confidential label to content (email or document)
- Protect content in any Office apps
- Use Microsoft Defender to protect content in third-party apps
- Protect containers (Teams, 365 groups, and SharePoint sites)
- Label and encrypt meeting invites and the replies in Teams
- Extend sensitivity labels to Power BI, Microsoft Purview Data map assets, and third-party apps and services
Sensitivity labels are also in the compliance center under solutions > information protection > labels.
5. Manage data access control
Two of the security issues I brought up earlier are from external access and guest users.
The good news is that you can easily manage both in the Teams admin center.
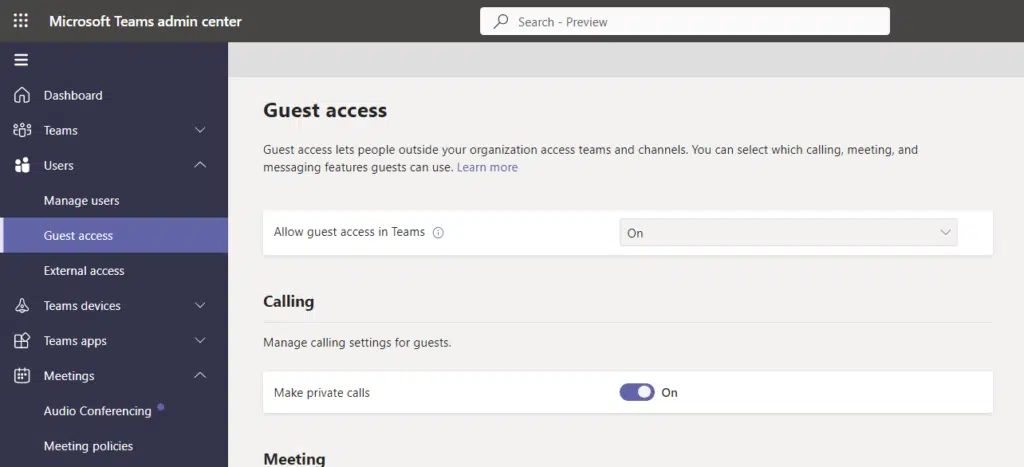
For the guest access settings, you can enable and disable the entire feature or become selective on what they can do in Teams:
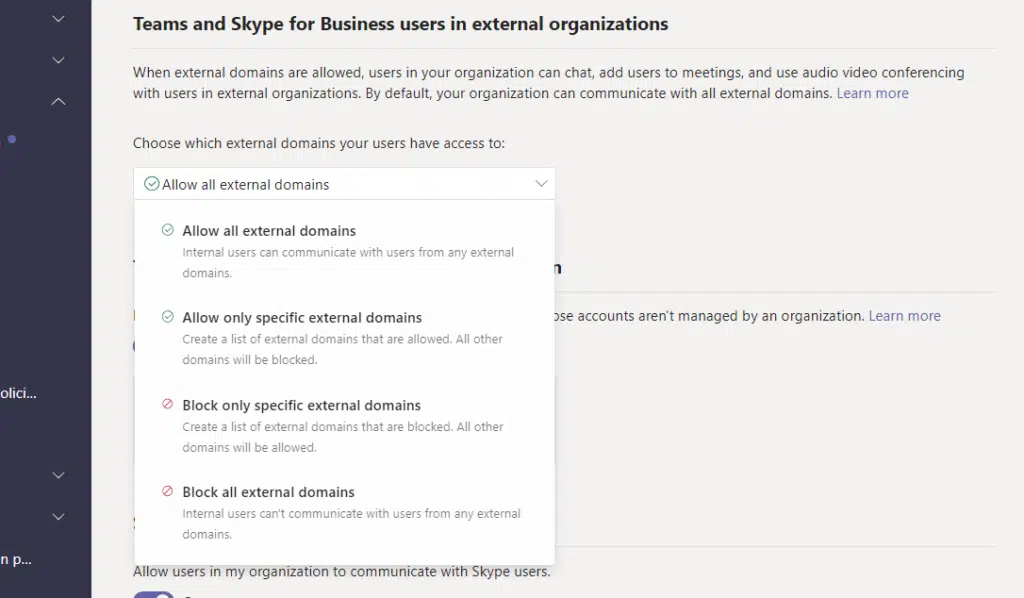
External access is a bit different and broader as it primarily allows communication with users outside your organization.
The settings you can change here are that you can specify the external domain that is permitted to communicate with your users.
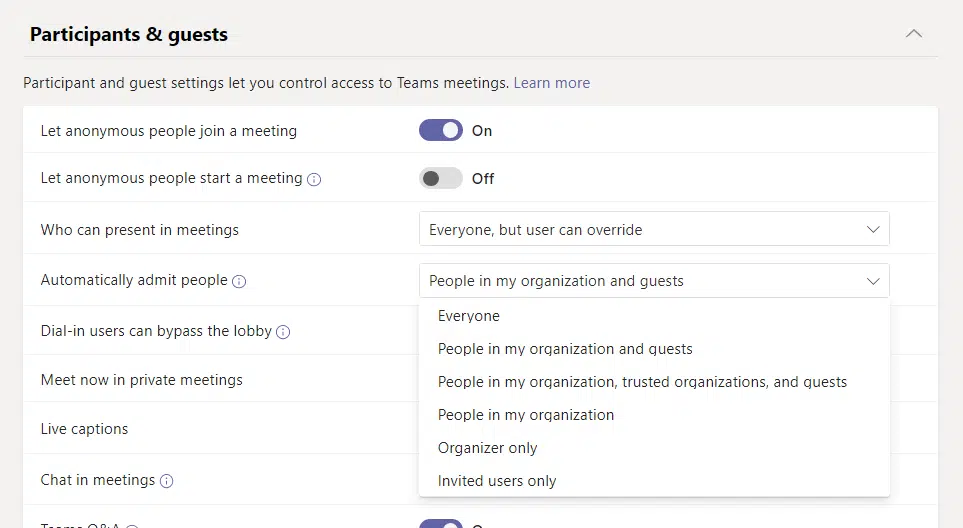
A bit related here is the lobby feature, which regulates who gets to be admitted to a meeting automatically.
You can find the option in Microsoft Teams admin center > meetings > meeting policies:
6. Enable multi-factor authentication
I didn’t mention this earlier since the chances are low. But it’s possible that your users might receive phishing attacks.
This is easy to counter since all you have to do is enable multi-factor authentication by default in the whole organization.
For this, you need to go to Azure Active Directory > Properties > Manage security defaults:
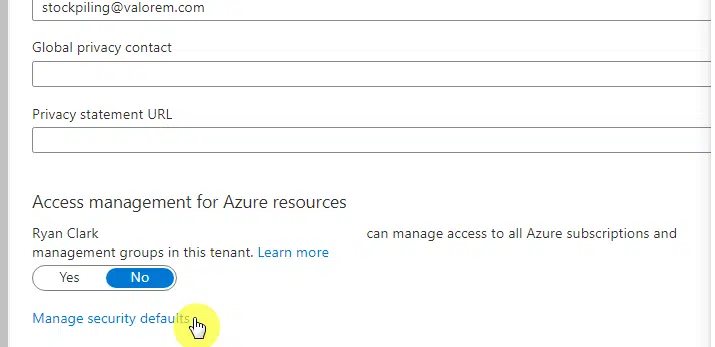
Choose the yes button on the slider on the right panel to enable security defaults. This will enforce MFA to all users.
However, if you enabled the per-user MFA feature, you need to turn it off before you can activate security defaults.
7. Audit user activity
It’s important to be aware of your user activity. Fortunately, there is an easy way to do this right inside the admin center.
Simply go to analytics and reports > usage reports and you will find various reports you can generate.
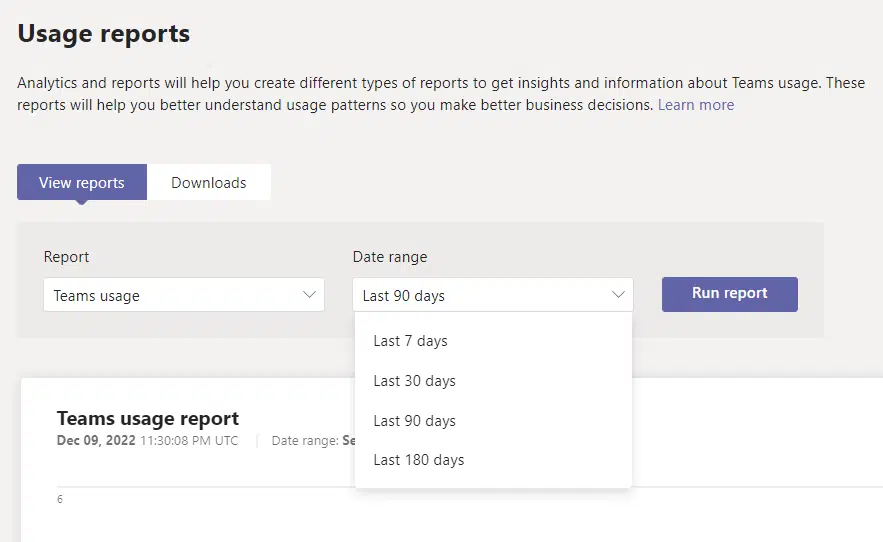
Currently, here are the reports you can generate:
- Apps usage
- PSTN blocked users
- PSTN minute and SMS pools
- PSTN and SMS usage
- Teams device usage
- Teams live event usage
- Teams usage
- Teams user activity
- Information protection license
- Virtual appointments usage
- Audio conferencing dial-out usage
You can use generated reports to check the behaviors of your users and what you can do to have better Microsoft Teams security.
8. Train your users
Lastly, it’s important that you teach your users Microsoft Teams security best practices so they can govern themselves.
All the implementations you will be doing would be pointless if users on the ground level won’t execute the policies.
At the very least, teach them about the following:
- Teams governance
- Access and permissions
- How to use Teams channels (including private channels)
- Managing files and apps
- Meetings and calls schedules and optimization
Following the #1 on this list also allows you to create a Microsoft Teams governance planning guide that you can share to your users.
Compliance and governance for Microsoft Teams security
Microsoft Teams security is actually beefy by default. In fact, it is compliant with a lot of standards like HIPAA, EUMC, ISO 27001, and more.
In terms of Microsoft Teams SEC compliance (and other related standards), Microsoft Purview Communication Compliance can help with that.
Although it doesn’t support end-to-end encryption yet, data is still encrypted (but can be decrypted by intermediate services).
Most of the security risks come from the side of users — both in terms of negligence and actual malicious content.
On the good side, you can implement best practices to reduce risk with Microsoft Teams:
- Define Microsoft Teams governance
- Identify sensitive data
- Set up app management
- Use data security features
- Manage data access control
- Enable multi-factor authentication
- Audit user activity
- Train your users
What do you think about the security risks in Microsoft Teams? Share your thoughts in the comments below.
For business inquiries, kindly send a message to me using the form on this page and I’ll get back to you asap.

